Cybersecurity researchers uncovered the “Xiū gǒu” phishing kit targeting users in the UK, US, Spain, Australia, and Japan. Active across public, postal, and banking sectors, the kit mimics legitimate services to harvest data.
Cybersecurity researchers at Netcraft have discovered a new phishing kit in action named “Xiū gǒu,” which has been actively targeting unsuspecting users in the UK, US, Spain, Australia, and Japan since September 2024.
This kit, notable for its unique branding and interactive features, has been identified in over 2,000 phishing websites, exposing both individuals and organizations across different sectors to the risk of being compromised.
The phishing kit, dubbed “Xiū gǒu” (修狗) after the Mandarin Chinese internet slang “xiū gǒu,” which translates to “doggo,” currently focuses on scams related to motorists, government payments, and postal services. The admin panel and associated Telegram account feature a cartoon dog mascot holding a soda bottle, adding an element of entertainment to the otherwise malicious tool.
According to the technical blog post shared with Hackread.com ahead of publishing on Thursday, Xiū gǒu’s front end utilizes Vue.js for both phishing pages and the admin panel, while the back end is powered by Golang through the SynPhishServer executable. This combination allows for a more active and harder-to-detect phishing infrastructure.
The kit has been deployed across more than 1,500 IP addresses and phishing domains, targeting victims with scams related to motorists, government payments, and postal services. Organizations in the public sector, postal, digital services, and banking sectors have been particularly vulnerable. Some of the notable impersonations include the following:
- Evri
- Linkt
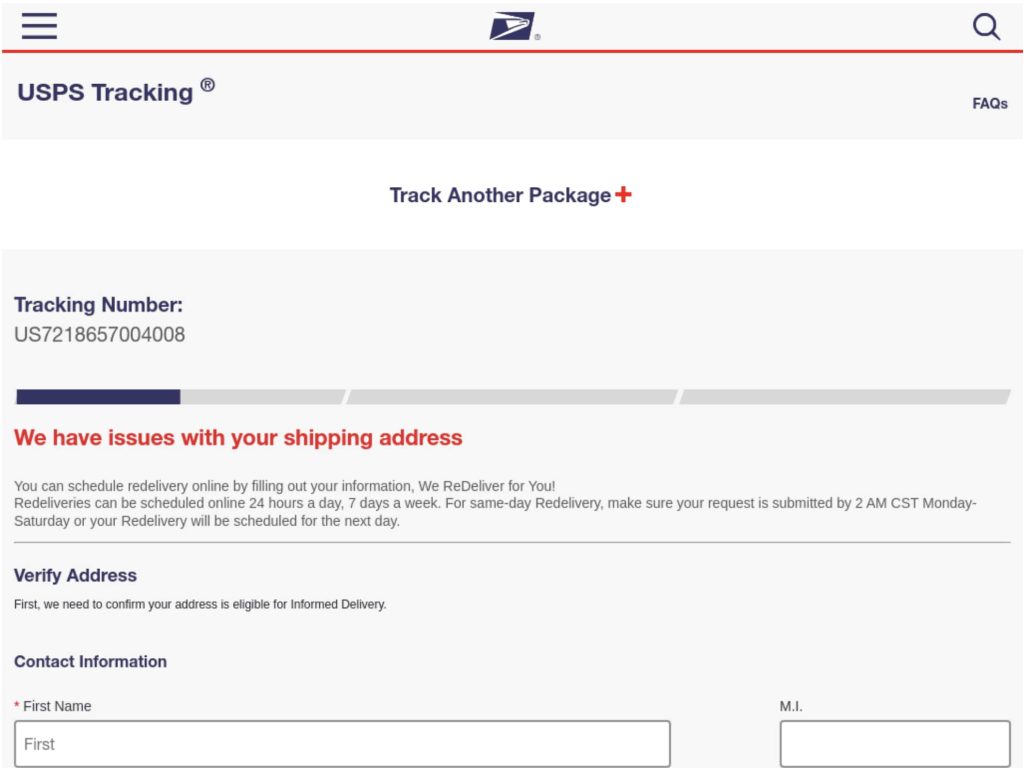
- USPS
- Lloyds
- Services Australia
- New Zealand Post
- UK Government (gov.uk and DVSA)
Threat actors using Xiū gǒu leverage Cloudflare’s anti-bot and hosting obfuscation capabilities to evade detection. They often register domains with the “.top” top-level domain (TLD), choosing names that relate to their scams, such as ‘parking’ or ‘living,’ or incorporating parts of the target brand’s name.
The attack flow typically begins with a Rich Communications Services (RCS) message containing a shortened link, which directs victims to a phishing website designed to mimic legitimate sites like gov.uk. Bots are redirected to non-malicious sites to further obfuscate the activity. Once victims enter their personal and payment details, the information is exfiltrated to Telegram via a bot set up by the fraudster.
Netcraft’s research provides a window into the minds of the kit’s authors stating, “Our research provides an interesting perspective into the minds and methods of the authors behind the kits and we can see by xiū gǒu’s use of specific scripting languages as well as the inclusion of user tutorials.“
“The author has also chosen to measure and analyze the use of their kit, most likely so that they can optimize and improve their competitiveness over time. We also get a sense of how—as with the doggo mascot—authors inject personality and humour into their kits, leaving their own distinctive mark.”
The Xiū gǒu phishing kit remains active and is part of an ongoing global campaign targeting both businesses and individuals. To protect yourself, use caution with unsolicited messages and follow these steps to avoid becoming its next victim:
- Verify Links Before Clicking: Always hover over links in emails or texts to check the actual URL, and avoid clicking shortened links unless verified. Phishing kits often use misleading URLs to trick users.
- Be Careful with Personal Information: Avoid entering sensitive information on websites reached through unsolicited messages, especially if the site requests personal or payment details.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of protection. Even if a phishing kit collects your credentials, MFA can help prevent unauthorized access to your accounts.
- Use Anti-Phishing Software: Many anti-phishing tools can detect suspicious sites and prevent you from accessing them, even if you accidentally click on a phishing link.
- Educate Yourself on Phishing Tactics: Stay informed about common phishing strategies and indicators, like unusual language or suspicious domain names, which can help you identify threats before they become issues.
RELATED TOPICS
- EvilProxy Phishing Kit Hits 100+ Firms as It Bypasses MFA
- Chinese ‘Smishing Triad’ Group Hits Pakistan with SMS Phishing
- V3B Phishing Kit Steals Logins and OTPs from EU Banking Users
- FishXProxy Phishing Kit Makes Phishing Ready for Script Kiddies
- EvilProxy Phishing Kit Targets Microsoft Users via Indeed.com Flaw
- Russian Hackers Employ Telekopye Toolkit in Broad Phishing Attacks
