A new ransomware strain called Nnice has emerged as a significant threat to Windows systems, employing sophisticated encryption techniques and evasion methods.
First observed on January 17, 2025, by CYFIRMA’s Research and Advisory team, Nnice has quickly gained attention in the cybersecurity community for its advanced capabilities.
Nnice targets Windows systems, encrypting files with a distinct “.xdddd” extension. The ransomware utilizes a hybrid encryption logic, combining Salsa20 and RSA-2048 algorithms for rapid and secure file encryption.
This approach leverages the speed of symmetric encryption (Salsa20) for bulk data encryption, while using asymmetric encryption (RSA-2048) for key management, a tactic similar to other sophisticated ransomware strains.
Cyfirma researchers noted that the ransomware’s encryption process is notably efficient, with researchers reporting that it can encrypt files in a matter of seconds rather than hours.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Encryption Methods
Nnice employs a three-step encryption method:-
- Encrypts a randomly generated RSA key using a built-in RSA key
- Encrypts a randomly generated RC4 key using the first RSA key
- Encrypts the victim’s files using the RC4 key
This multi-layered approach makes decryption extremely challenging without the attacker’s private key.
Nnice demonstrates advanced evasion techniques, including the ability to stop services and terminate processes that might interfere with file encryption. It also creates child processes to confuse debugging tools, mimicking legitimate system services to blend in with normal operations.
.webp)
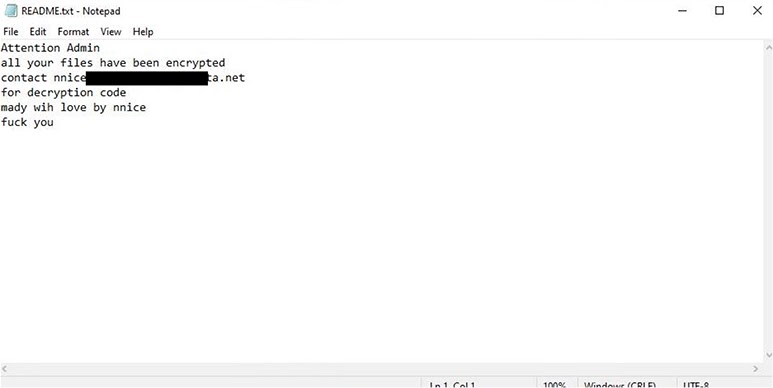
The ransomware’s attack vector remains unclear, but it likely spreads through phishing emails or exploits in vulnerable systems. Once executed, Nnice changes the victim’s desktop wallpaper and leaves a ransom note titled “Readme.txt” with instructions for file recovery.
.webp)
Notably, Nnice employs various encryption modes, including Full, Partial, and Smart. The Smart method uses intermittent technology to accelerate encryption by only encrypting certain parts of files or data. This technique allows for faster encryption while still rendering files unusable.
CYFIRMA researchers have identified several MITRE ATT&CK techniques used by Nnice, including:-
- T1486: Data Encrypted for Impact
- T1490: Inhibit System Recovery
- T1055: Process Injection
- T1562: Impair Defenses
- T1070: Indicator Removal
The ransomware also attempts to gain special permissions to the root directory, enhancing its ability to encrypt critical system files.
Cybersecurity experts recommend implementing robust backup systems, keeping software updated, and employing advanced threat detection tools to mitigate the risk of ransomware attacks.
Organizations are advised to stay vigilant and implement comprehensive ransomware prevention and recovery strategies to protect against this emerging threat.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar




