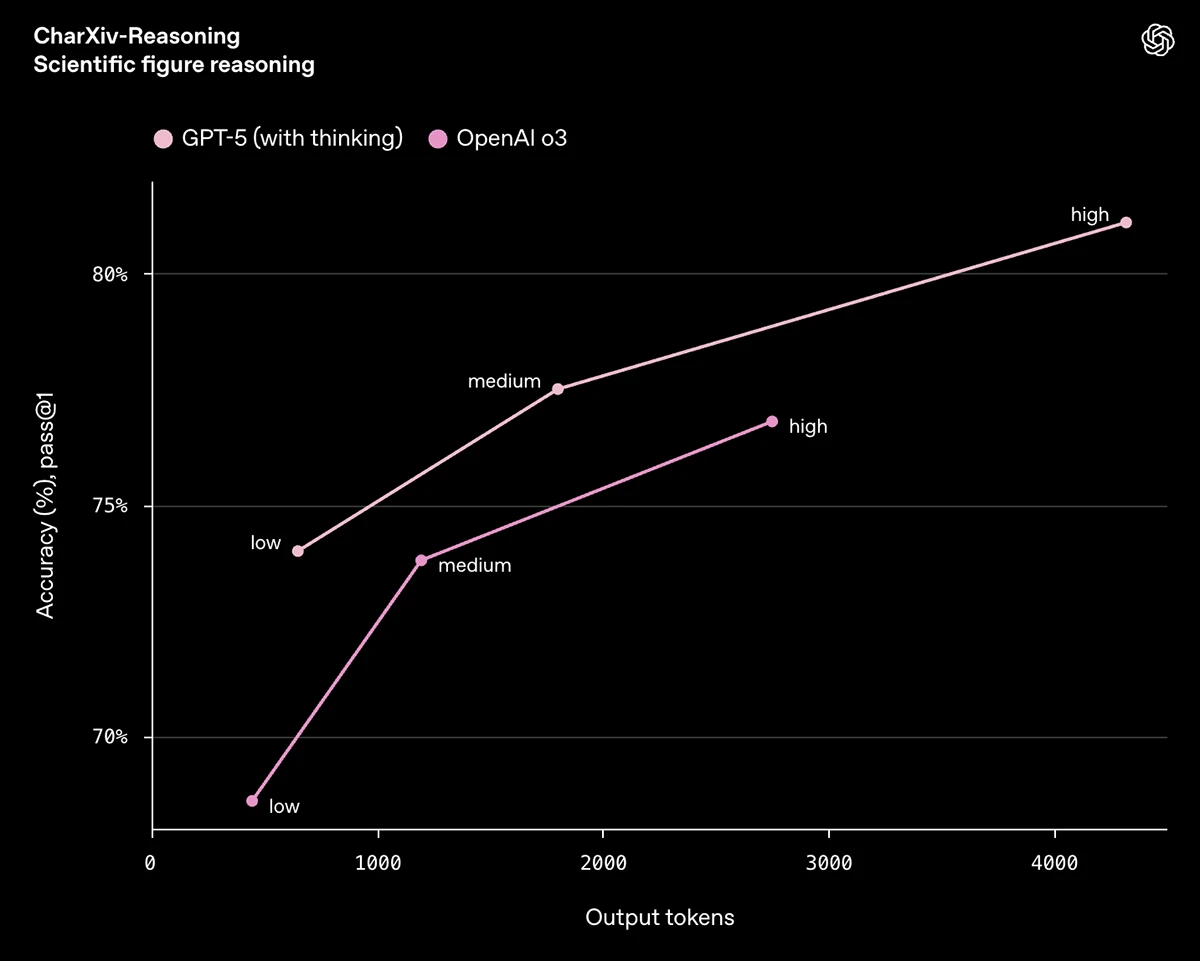
After a long wait, GPT-5 is finally rolling out. It’s available for free, Plus, Pro and Team users today. This…
For this reason, Murgatroyd noted that purchasers of TETRA-based radios are free to deploy other solutions for end-to-end encryption on…
Elite cybercriminals prefer LotL attacks because they’re incredibly hard to spot. Instead of deploying obvious malware, attackers use the same…
Aug 07, 2025Ravie LakshmananMalware / Threat Intelligence The threat actors behind the SocGholish malware have been observed leveraging Traffic Distribution…
A string of previously undisclosed break-ins at Tennessee National Guard armories last fall marks the latest in a growing series…
Splunk has introduced PLoB (Post-Logon Behaviour Fingerprinting and Detection) in a world where compromised credentials remain the primary vector for…
OpenAI has released GPT‑5, the newest version of its large language model. It’s now available to developers and ChatGPT users,…
A new Endpoint Detection and Response (EDR) killer that is considered to be the evolution of ‘EDRKillShifter,’ developed by RansomHub, has…
Threat actors are increasingly using Scalable Vector Graphics (SVG) files to get beyond traditional defenses in the quickly developing field…
Bouygues Telecom warns it suffered a data breach after the personal information of 6.4 million customers was exposed in a cyberattack….
Cybersecurity firm SonicWall has officially addressed recent concerns about a potential new zero-day vulnerability in its Secure Sockets Layer Virtual…
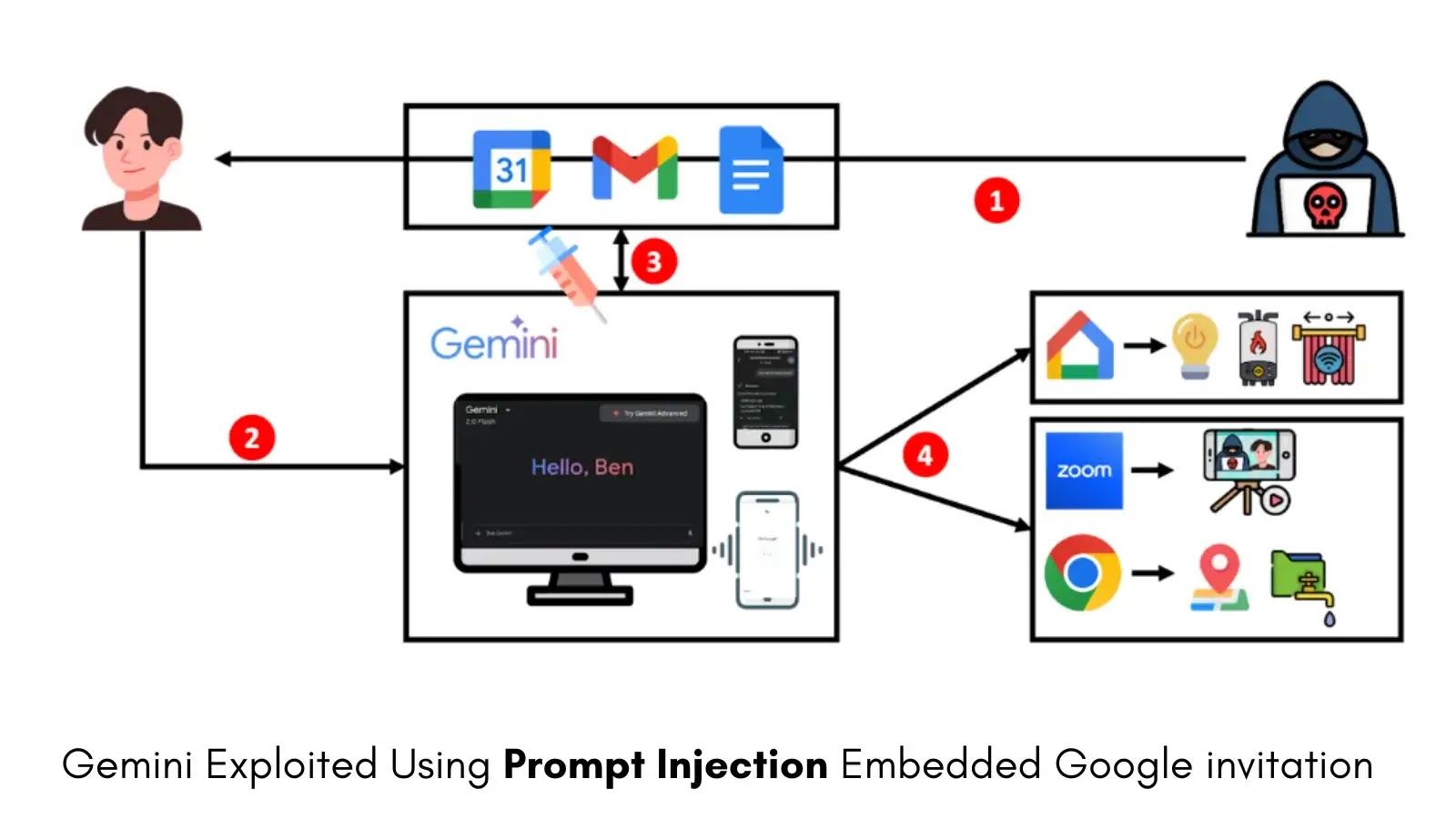
Security researchers have discovered a series of critical vulnerabilities in Google’s Gemini AI assistant that allow attackers to exploit the…