By Nadir Izrael, Co-Founder and CTO, Armis The threat of cyber warfare against Australia has escalated, driving a significant increase…
A critical security vulnerability in Microsoft Remote Desktop Client could allow attackers to execute arbitrary code on victim systems. The…
A critical security vulnerability has been discovered in Citrix’s Windows Virtual Delivery Agent that could allow attackers with low-level system…
In this Help Net Security interview, Dr. Nicole Nichols, Distinguished Engineer in Machine Learning Security at Palo Alto Networks, discusses…
A critical security vulnerability has been discovered in Fortinet’s FortiWeb web application firewall that allows unauthenticated attackers to execute malicious…
In a significant development in international cybercrime efforts, Xu Zewei, a 33-year-old Chinese national, was apprehended in Milan, Italy, on…
Cybersecurity friction usually gets framed as a user problem: password policies that frustrate employees, MFA that slows down logins, or…
Security researchers have uncovered two significant vulnerabilities in Zoom Clients for Windows, exposing users to potential Denial of Service (DoS)…
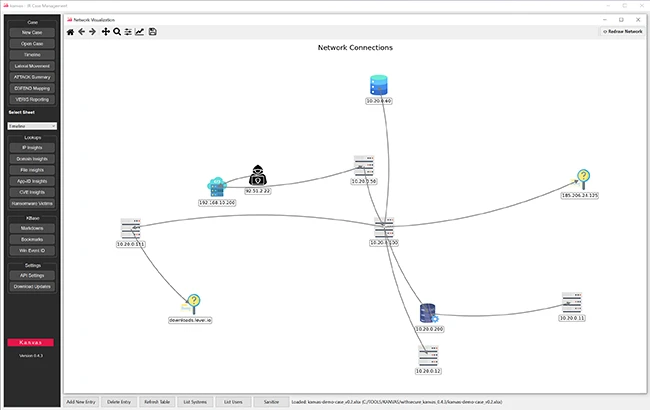
Kanvas is an open-source incident response case management tool with a simple desktop interface, built in Python. It gives investigators…
AI is changing how we detect, prevent, and respond to cyber threats. From traditional networks to emerging spaces, it is…
As much as AI has captured the imagination of Australian business leaders, there is a sobering reality: most organisations are…
TAFE NSW is to spend $34.1 million on Microsoft cloud and digital services over the next three years under a…