In April 2025, at the ITER Private Sector Fusion Workshop in Cadarache, something remarkable unfolded. In a room filled with…
The advanced Graphite mercenary spyware, developed by Paragon, targets journalists through a sophisticated zero-click vulnerability in Apple’s iOS. At least…
HiddenLayer’s security research team has uncovered TokenBreak, a novel attack technique that bypasses AI text classification models by exploiting tokenization…
Cybersecurity researchers have uncovered a sophisticated ransomware campaign targeting utility billing software providers through unpatched vulnerabilities in SimpleHelp Remote Monitoring…
Microsoft addressed a high-severity elevation of privilege vulnerability (CVE-2025-21420) in its Windows Disk Cleanup Utility (cleanmgr.exe) during February 2025’s Patch…
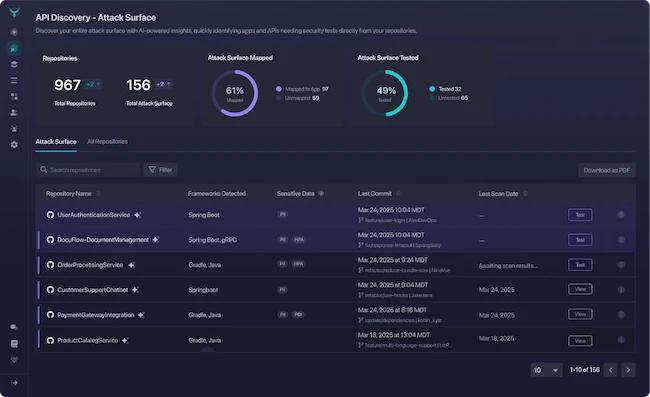
StackHawk announced Sensitive Data Identification to give security teams visibility into high-risk APIs across thousands of code repositories within an…
Apple has disclosed that a now-patched security flaw present in its Messages app was actively exploited in the wild to…
Panel members on the AI as a Competitive Advantage session held at the AI Summit in London this week discussed…
Trend Micro fixes critical bugs in Apex Central and TMEE PolicyServer Pierluigi Paganini June 13, 2025 Trend Micro fixed multiple…
The Fog ransomware group has evolved beyond conventional attack methods, deploying an unprecedented arsenal of legitimate pentesting tools in a…
On June 12, 2025, concurrent infrastructure failures at Cloudflare and Google caused widespread service disruptions, highlighting vulnerabilities in modern cloud…
Here’s a look at the most interesting products from the past week, featuring releases from Contrast Security, Cymulate, Lemony, SpecterOps,…