A critical vulnerability in the GNU C Library (glibc), potentially exposing millions of Linux systems to local privilege escalation attacks. …
As a website owner, one of my top priorities is to ensure that my website is protected from cyber threats….
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
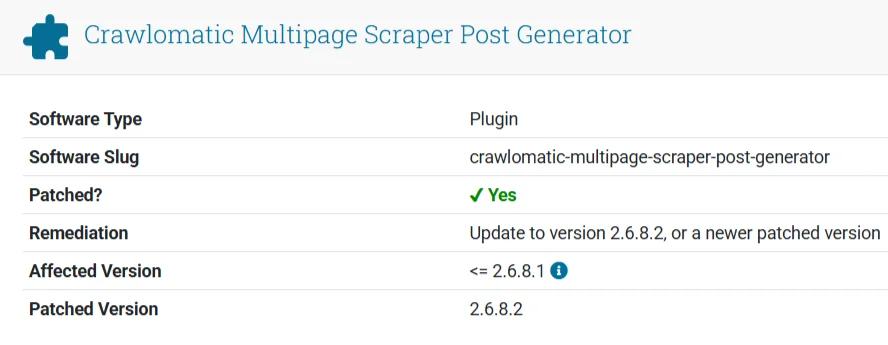
A severe security vulnerability has been discovered in the popular WordPress plugin, Crawlomatic Multisite Scraper Post Generator, potentially placing thousands…
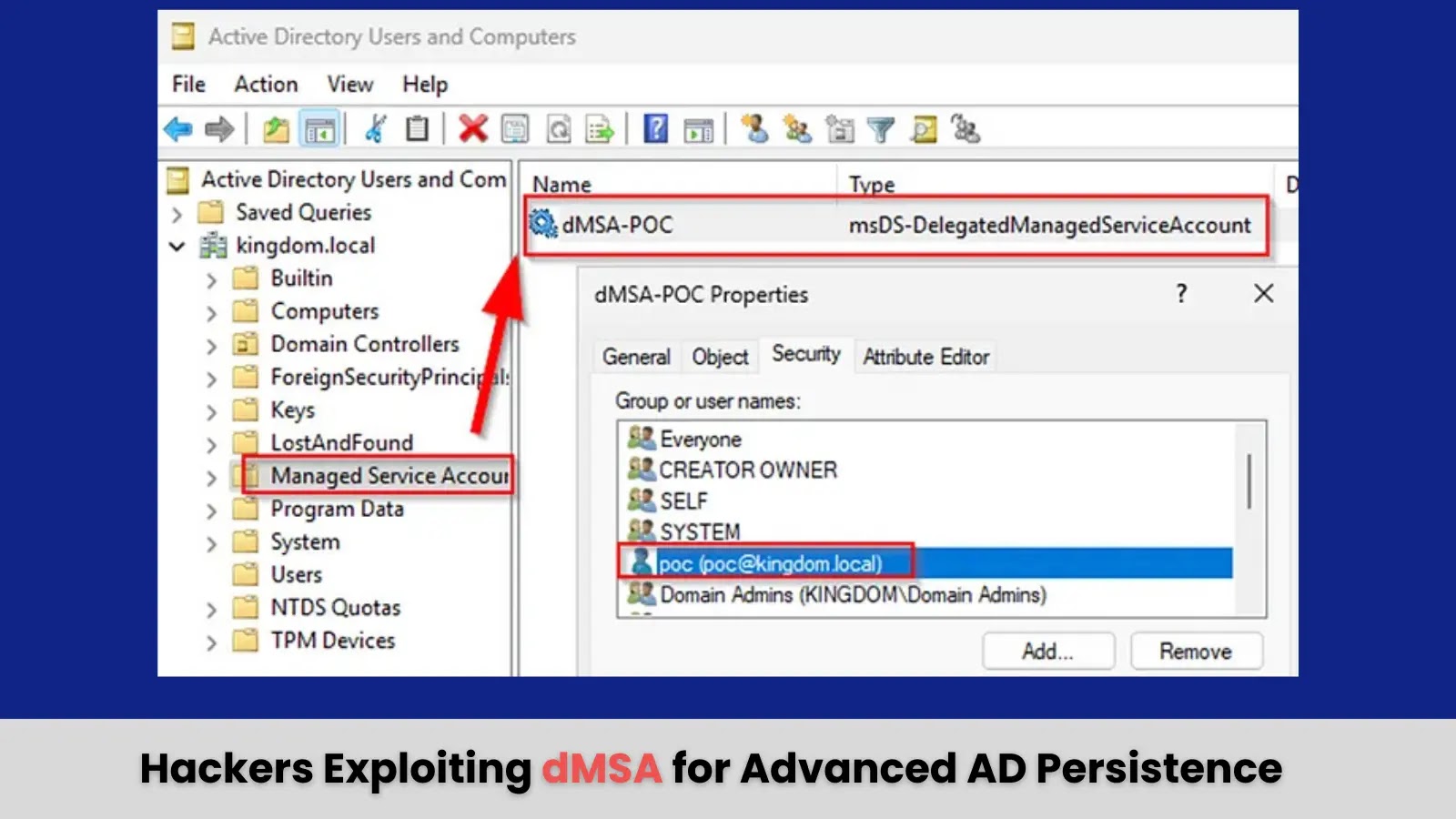
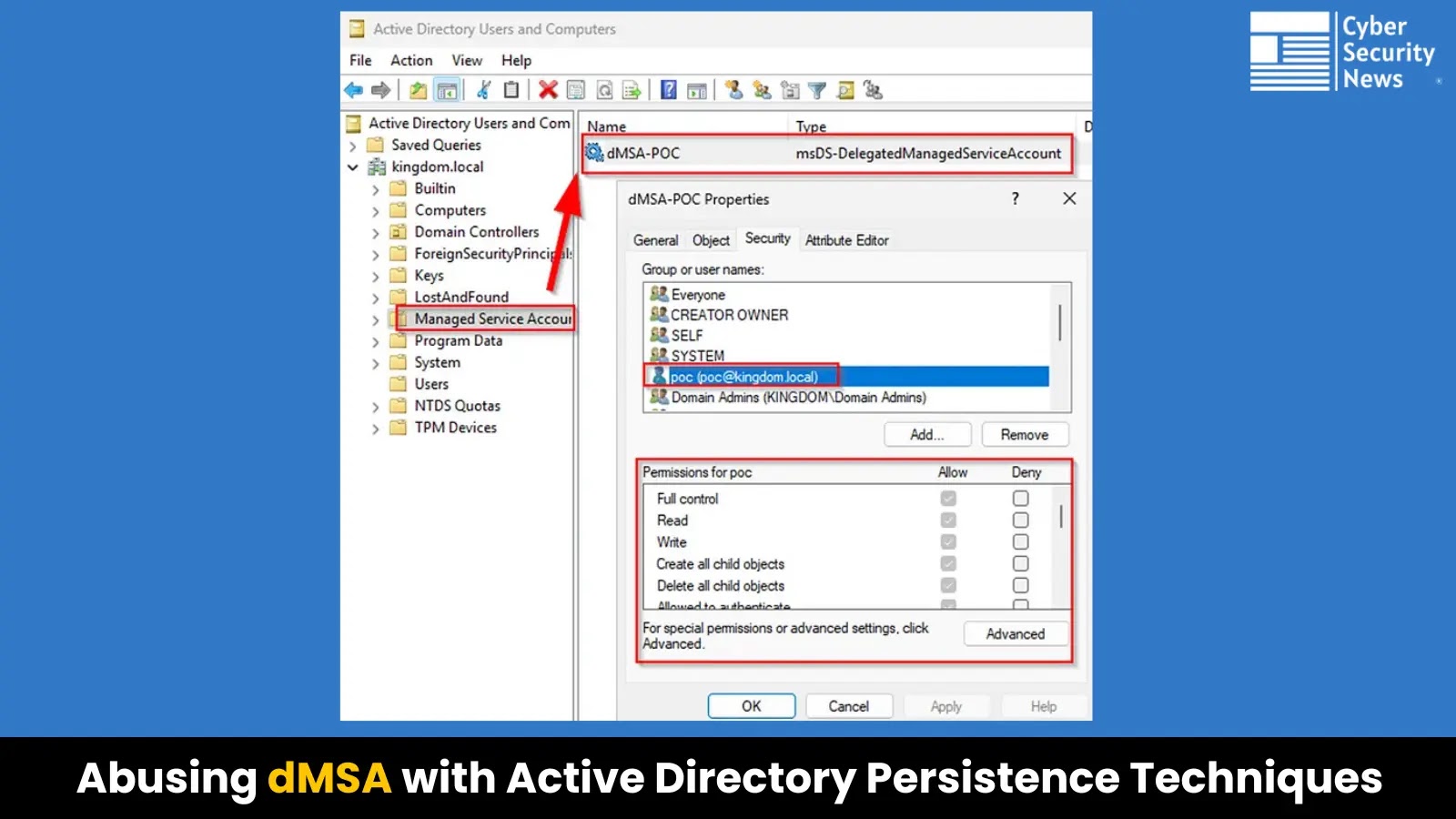
Security researchers have identified new methods for achieving persistence in Active Directory environments by exploiting Delegated Managed Service Accounts (dMSAs),…
Eric Council Jr., a 26-year-old from Athens, Alabama, has been sentenced to 14 months in federal prison. He played a…
Delegated Managed Service Accounts (dMSAs), introduced in Windows Server 2025, represent Microsoft’s latest innovation in secure service account management. While…
Security researchers have disclosed a significant vulnerability in the GNU C Library (glibc), potentially affecting millions of Linux systems worldwide….
Cybersecurity threats are an ever-present danger in today’s interconnected world, and one of the most insidious types of breaches involves…
In this Help Net Security interview, Full Professor at University of Leuven, unpacks the European Commission’s encryption agenda, urging a…
A recent cyberattack on Marks and Spencer (M&S) has raised significant concerns, revealing that hackers infiltrated the UK-based retailer’s systems…
AI systems can sometimes produce outputs that are incorrect or misleading, a phenomenon known as hallucinations. These errors can range…