A malicious package in the Node Package Manager index uses invisible Unicode characters to hide malicious code and Google Calendar links…
A sophisticated cyberespionage campaign, dubbed Operation RoundPress, has been uncovered by cybersecurity researchers at ESET. Attributed with medium confidence to…
FrigidStealer malware targets macOS users via fake browser updates, stealing passwords, crypto wallets, and notes using DNS-based data theft methods….
More CISOs than ever—80 percent—see human risk, in particular negligent employees, as the most serious vulnerability. Cybercrime is big business. Cybersecurity…
May 15, 2025Ravie LakshmananMalware / Threat Intelligence Cybersecurity researchers have discovered a malicious package named “os-info-checker-es6” that disguises itself as…
A formidable new malware loader, dubbed TransferLoader, has emerged as a significant cybersecurity threat, as detailed in a recent report…
Credential protection is key to preventing breaches. Secure APIs, rotate secrets and train devs to handle credentials safely and efficiently….
Companies running Samsung MagicINFO, a platform for managing content on Samsung commercial digital displays, should upgrade to the latest available…
A Russia-linked threat actor has been attributed to a cyber espionage operation targeting webmail servers such as Roundcube, Horde, MDaemon,…
Cybercriminals aren’t so different from the rest of us — they live in the real world, and their spending and investment…
Over the years, many different technologies have transitioned to Cloud-based solutions, including ERP systems and email management platforms. Phone systems…
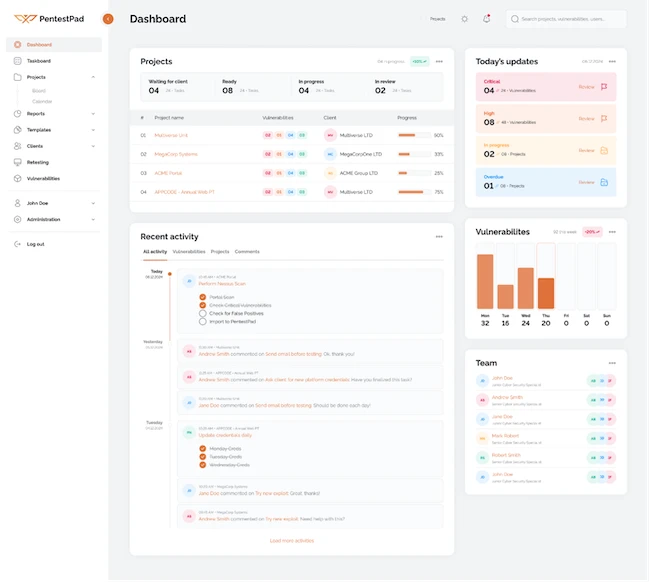
PentestPad announced a major rollout of new features to its platform, built to transform how modern security teams deliver penetration…