Trend Micro fixes critical bugs in Apex Central and TMEE PolicyServer Pierluigi Paganini June 13, 2025 Trend Micro fixed multiple…
The Fog ransomware group has evolved beyond conventional attack methods, deploying an unprecedented arsenal of legitimate pentesting tools in a…
On June 12, 2025, concurrent infrastructure failures at Cloudflare and Google caused widespread service disruptions, highlighting vulnerabilities in modern cloud…
Here’s a look at the most interesting products from the past week, featuring releases from Contrast Security, Cymulate, Lemony, SpecterOps,…
A critical zero-day vulnerability in WebDAV implementations that enables remote code execution, with proof-of-concept exploit code now publicly available on…
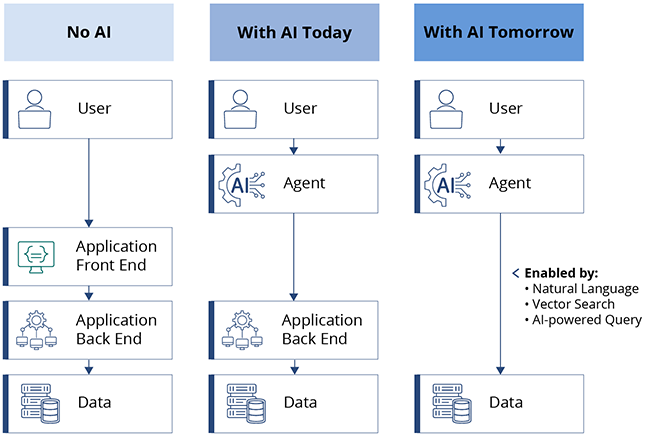
GenAI has been the star of the show lately. Tools like ChatGPT impressed everyone with how well they can summarize,…
In this Help Net Security interview, Amichai Shulman, CTO at Nokod Security, discusses how the abstraction layer in no-code environments…
The Australian Signals Directorate (ASD) says it is aware of cybercriminals claiming to be them through emails and phone calls,…
Cybersecurity researchers have uncovered a sophisticated malware campaign that leveraged an advanced JavaScript obfuscation technique to compromise hundreds of legitimate…
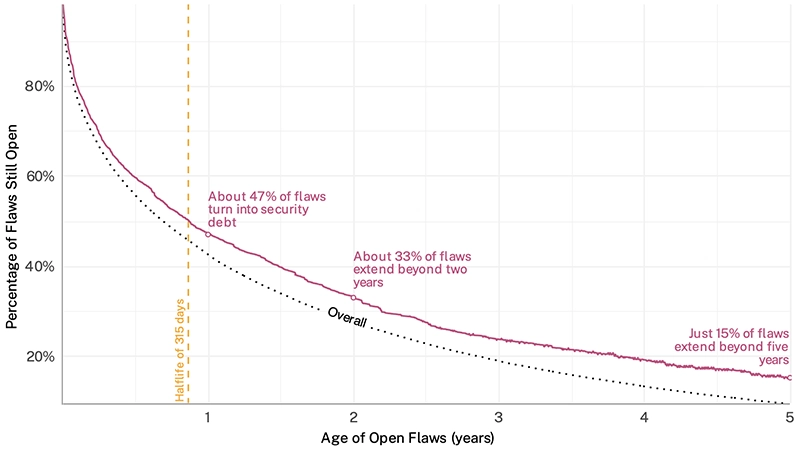
78% of public sector organizations are operating with significant security debt, flaws left unaddressed for more than a year, according…
In today’s rapidly evolving technological landscape, businesses need more than just products; they need comprehensive solutions that foster agility, security…
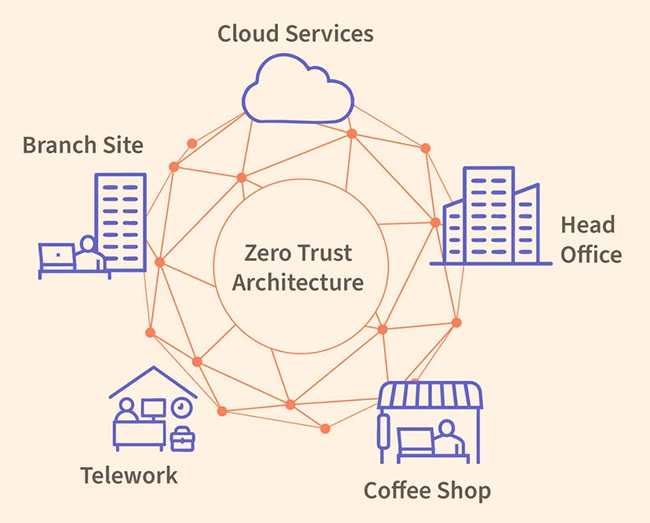
The National Institute of Standards and Technology (NIST) has released a new guide that offers practical help for building zero…