Robert Woodford, a recruitment marketing specialist, recently shared on LinkedIn how he fell victim to a highly sophisticated scam while…
Jun 06, 2025The Hacker NewsArtificial Intelligence / Zero Trust When generative AI tools became widely available in late 2022, it…
The Qilin ransomware operation has recently joined attacks exploiting two Fortinet vulnerabilities that allow bypassing authentication on vulnerable devices and…
A significant security vulnerability affecting millions of Chrome extension users has been discovered, revealing widespread exposure of sensitive API keys,…
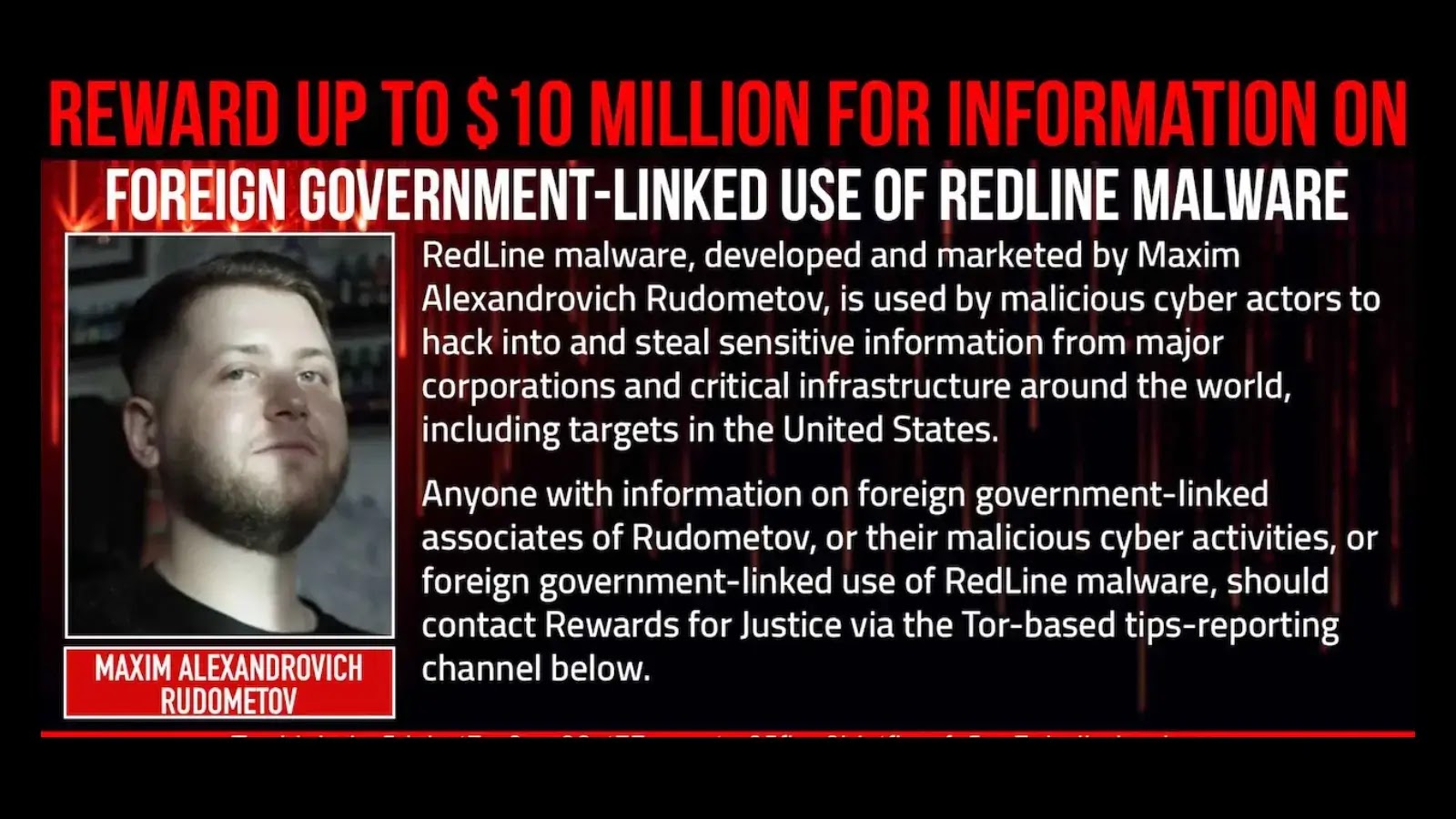
The US State Department has announced a reward of up to $10 million for information leading to the identification or…
iVerify’s NICKNAME discovery reveals a zero-click iMessage flaw exploited in targeted attacks on US & EU high-value individuals including political…
Multiple severe security vulnerabilities in HPE Insight Remote Support (IRS) platform that could allow attackers to execute remote code, traverse…
HUMAN’s Satori Threat Intelligence and Research team, in collaboration with Google, Trend Micro, and Shadowserver, has uncovered and partially disrupted…
“Cybercrime is rising and SMBs rely on MSPs to provide the security tools and services they can’t staff or build themselves,”…
Millions of Internet-of-Things (IoT) devices running the open-source version of the Android operating system are part of the Badbox 2.0…
In a time when digital transformation is the backbone of public services, Chief Information Security Officers (CISOs) in government and…
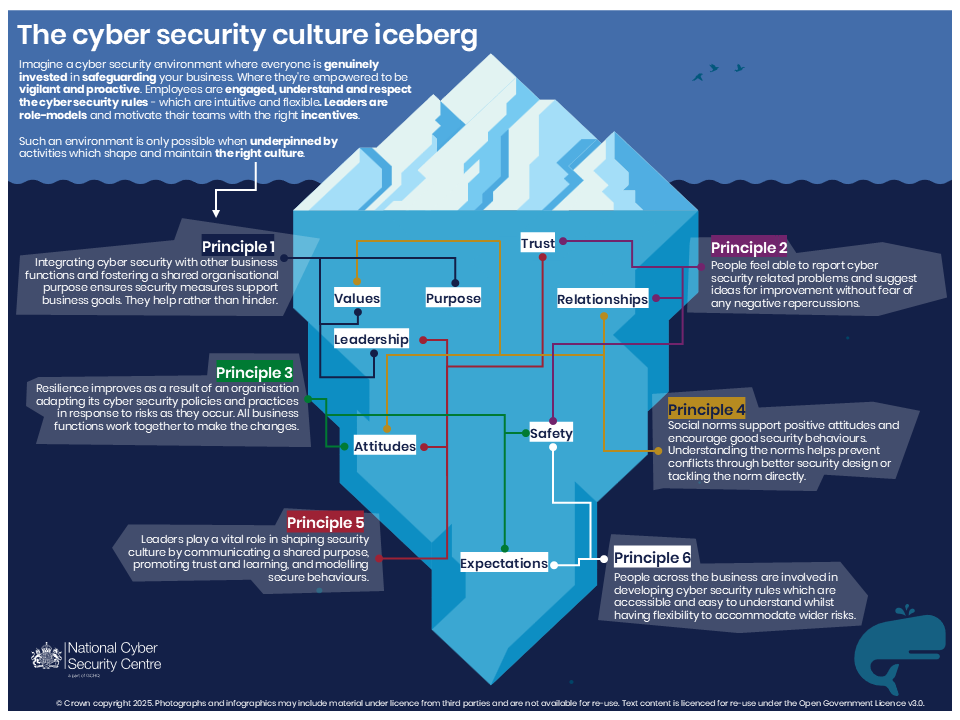
The UK’s National Cyber Security Centre (NCSC) has introduced a set of six core principles to help organizations embed strong…