A cascading supply chain attack on GitHub that targeted Coinbase in March has now been traced back to a single…
A recent cyberattack campaign leveraging the DarkCloud stealer has been identified, targeting Spanish companies and local offices of international organizations…
Jacksonville, United States, April 3rd, 2025, CyberNewsWire Secure Ideas, a premier provider of penetration testing and security consulting services, proudly…
I’ve been a role-player since 7th grade and had the good fortune of being indoctrinated into a very elite form…
Kaspersky Lab has uncovered a new version of the Triada Trojan, a sophisticated malware targeting Android devices. This variant has…
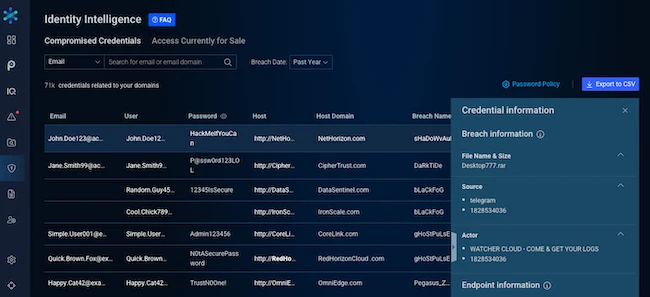
Bitsight launched Bitsight Identity Intelligence, a new, standalone threat intelligence module designed to help security teams detect compromised credentials, prevent…
Not one but several worried parents that tracked their children by using T-Mobile tracking devices suddenly found that they were…
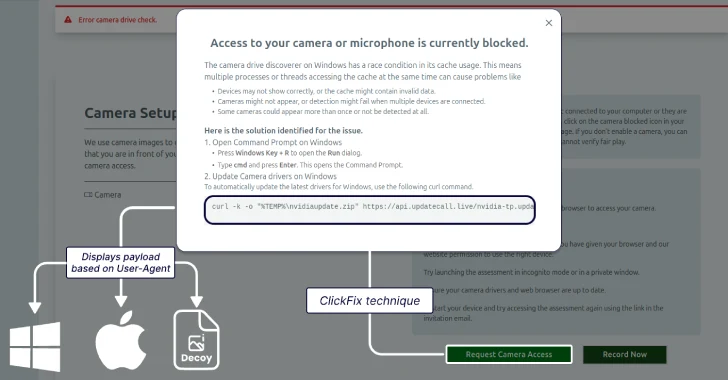
The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job…
As a consultant, the one thing I really miss is the feeling of owning a network and defending it. In…
Cisco has disclosed a significant vulnerability in its AnyConnect VPN Server for Meraki MX and Z Series devices, allowing authenticated attackers to…
Artificial Intelligence has rapidly become the linchpin of the financial sector, transforming traditional processes and creating novel opportunities across industries….
CVE-2024-20439, a static credential vulnerability in the Cisco Smart Licensing Utility, is being exploited by attackers in the wild, CISA…