A sophisticated remote access trojan (RAT) dubbed SnowDog has surfaced on underground cybercrime forums, prompting alarms among cybersecurity experts. Advertised as a…
As I’ve mentioned in previous posts, I’m back playing Table Tennis. The group I’m playing with now is the best…
Tom Ryder | 03 April 2025 at 09:17 UTC PortSwigger’s Vision In March, PortSwigger hosted its biggest webinar to date…
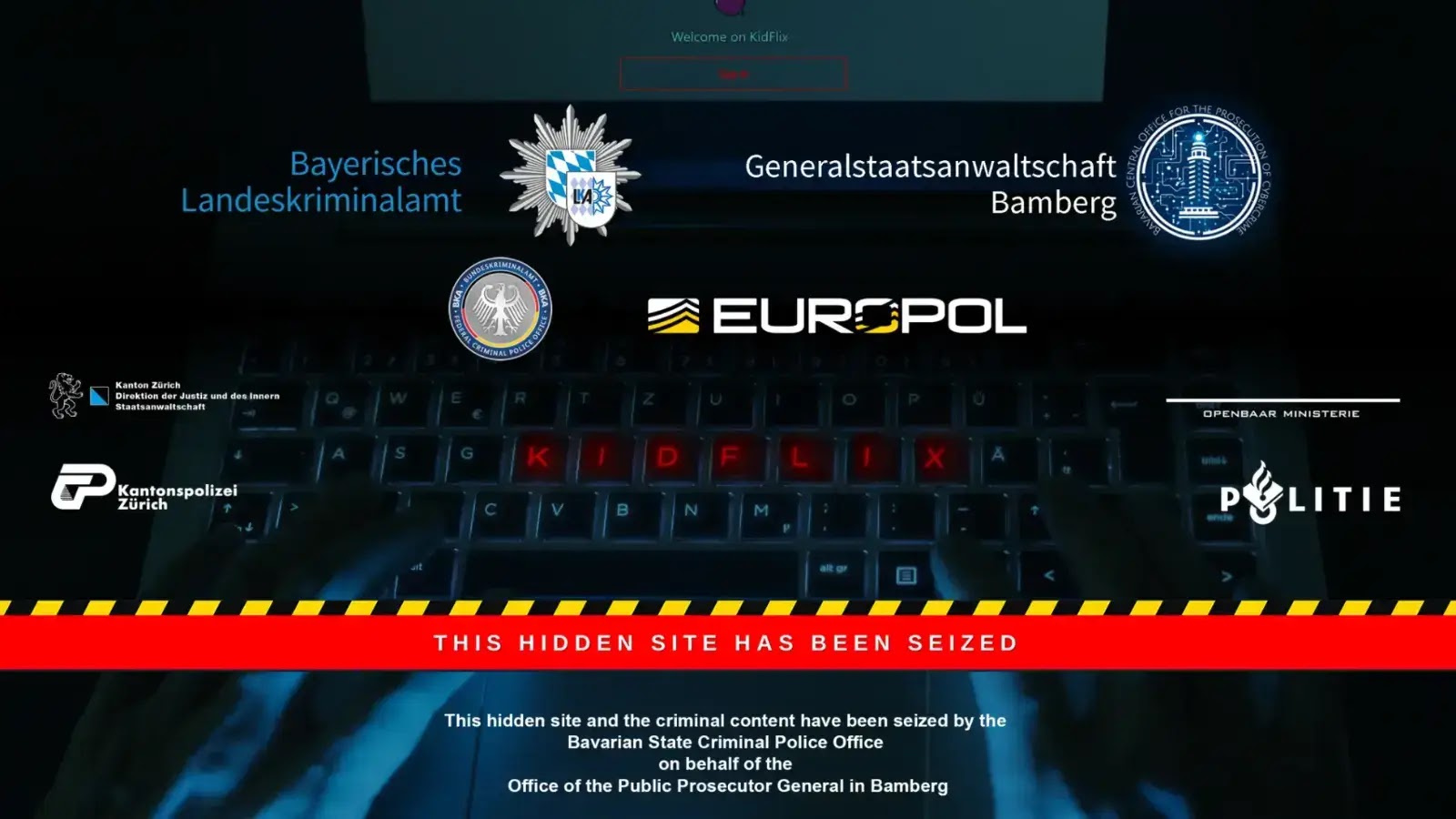
In one of the most significant operations against child sexual exploitation in recent history, authorities have announced the shutdown of…
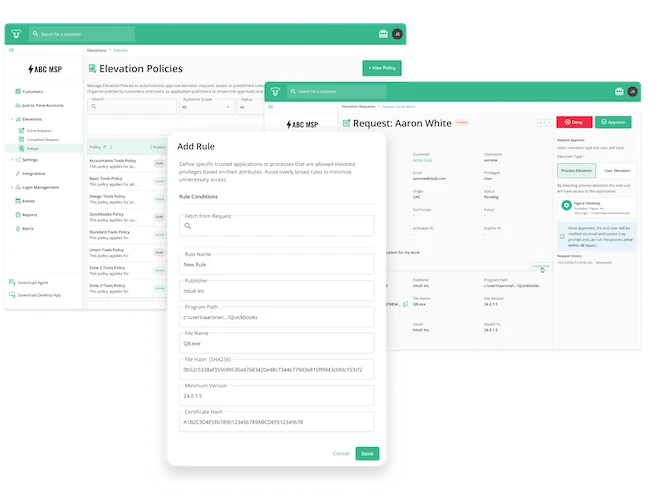
CyberQP has launched its Zero Trust Helpdesk Security Platform—combining QGuard for Privileged Access Management (PAM) and QDesk for End-User Access…
Apr 03, 2025Ravie LakshmananData Privacy / Vulnerability Cybersecurity researchers have disclosed details of a new vulnerability impacting Google’s Quick Share…
Giving autistic children the opportunity to experience a major sporting event in a safe environment is the latest project in…
I’ve been using TextWrangler for a while now — a free uber-text editor that’s used heavily by web developers. It’s…
A vulnerability in Verizon’s Call Filter app for iOS has been discovered, allowing unauthorized access to customer call logs. This…
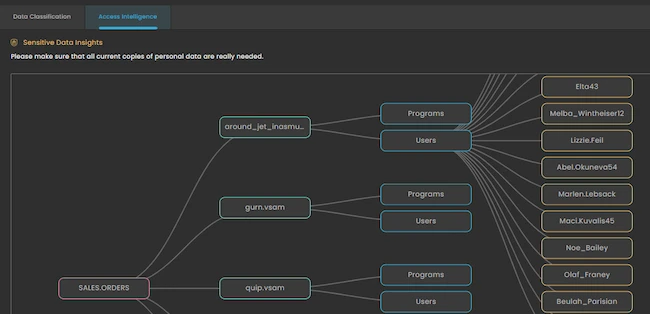
1touch.io launched the next-generation Enterprise Data Security Posture Management (DSPM) platform, a solution designed specifically for hybrid, multi-cloud, on-premises, and…
Over the years I’ve noticed something a bit peculiar about myself when it comes to striving for outcomes. In short,…
CVSS stands for ‘Common Vulnerability Scoring System’. The CVSS framework is an open cyber security framework owned by a US-based…