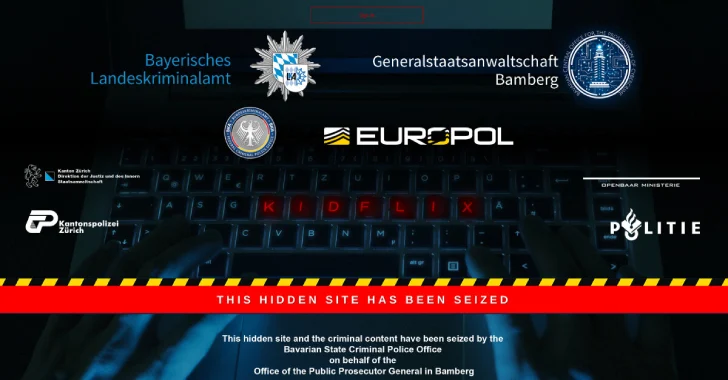
In one of the largest coordinated law enforcement operations, authorities have dismantled Kidflix, a streaming platform that offered child sexual…
New Triada Trojan comes preinstalled on Android devices Pierluigi Paganini April 03, 2025 A new Triada trojan variant comes preinstalled…
I’ve always been obsessed with time and location. For as long as I can remember, I’ve always been fascinated with…
Cybersecurity isn’t what it used to be. Attackers are moving quicker, disruptions happen all the time, and many security plans…
Apr 03, 2025Ravie LakshmananCybersecurity / Threat Intelligence Threat hunters are warning of a sophisticated web skimmer campaign that leverages a…
Most people, whether they admit to it or not, enjoy learning about their birthdays and/or who shares them. Well, I…
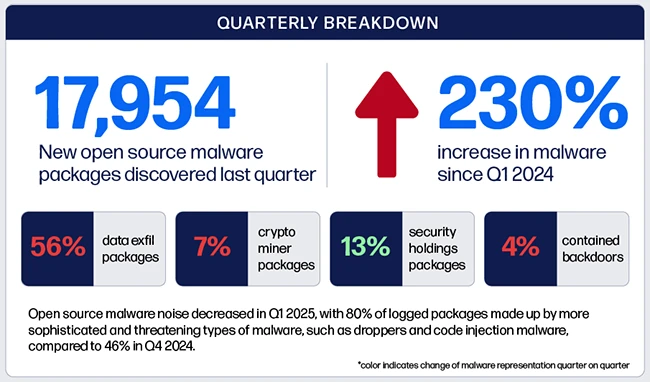
There’s been a notable shift in the types of threats targeting software developers, with a total of 17,954 open source…
Someone pointed out this Gentoo flame article the other day and I just got around to finally reading it. Well,…
Zero to Engineer is a practical guide for anyone looking to launch a career in information technology without a traditional…
I just got back from the grocery store, and I feel like utter crap. My girlfriend and I were in…
Monash College overhauled its enterprise performance management as part of a broader finance transformation, helping it navigate and forecast the…
So I’ve had a theory for many years now. It’s not particularly poignant or anything, but I figured it’s my…