I tend to shy away from groupthink oriented idealogies, but ocassionally I am stricken by a concept that is worth…
One of the coolest things in Firefox is its ability to do Google searches via the address bar; I use…
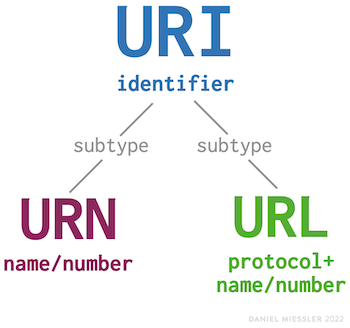
A URL is a subtype of URI that includes a protocol, like FTP or HTTP Updated: October 10, 2023 URI…
As I covered to some degree in an earlier post, quicksearches are quite sick. They let you search sites from…
HijackLoader, a malware loader first identified in 2023, has undergone significant evolution with the addition of new modules designed to…
Well, I just passed the final exam for the GIAC GSEC credential from SANS, and I have to say it’s…
Witnesses at a House hearing on medical device cybersecurity Tuesday called out the need for more proactive tracking of products…
A critical vulnerability has been identified in the Plantronics Hub software, a client application commonly used to configure Plantronics audio…
Something struck me the other day that I think most power-users with experience on both Windows and OS X would…
APT34, also known as OilRig or Helix Kitten, has intensified its cyber-espionage campaigns, deploying custom malware to target entities within…
There are many views on what constitutes a Vulnerability Assessment versus a Penetration Test. The main distinction, however, seems to…
Cybersecurity experts at eSentire’s Threat Response Unit (TRU) uncovered a sophisticated malware campaign leveraging KoiLoader, a malicious loader designed to…