Cybersecurity has become a leading priority for manufacturers of embedded systems and IoT devices. The rapid proliferation of these technologies,…
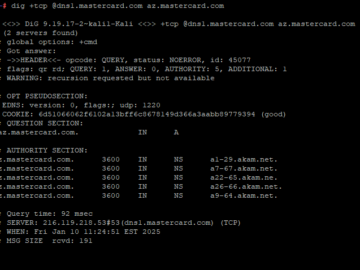
The payment card giant MasterCard just fixed a glaring error in its domain name server settings that could have allowed…
Researchers have uncovered two Mirai-based botnets harnessing Internet of Things (IoT) devices to DDoS target organizations around the world. The…
One of the most successful forms of password breaches occurs when hackers simply guess commonly used passwords. And while organizations…
As more aspects of daily life move online—including financial transactions, government services like mobile driver’s licenses, and digital travel authentication—the…
Back in the pre-internet days of the early 1990s, retail loyalty programmes were prehistoric (Green Shield stamps anyone?) – until…
The Alabama Community College System in partnership with Advantage Consulting & Solutions is set to debut its inaugural class of…
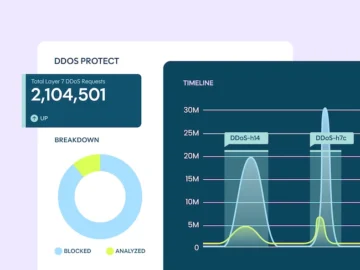
DataDome unveiled DDoS Protect, a cloud-based service designed to block distributed denial-of-service (DDoS) attack traffic at the edge before it…
A patch is available for a vulnerability in 7-Zip that could have allowed attackers to bypass the Mark-of-the-Web (MotW) security…
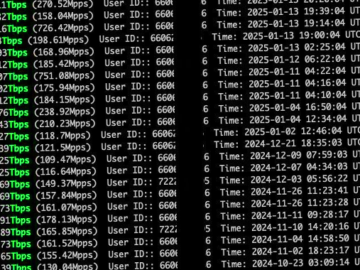
Threat actors are exploiting an unspecified zero-day vulnerability in Cambium Networks cnPilot routers to deploy a variant of the AISURU…
A new ransomware threat dubbed “Helldown” has emerged, actively exploiting vulnerabilities in Zyxel firewall devices to breach corporate networks. Cybersecurity…
As we navigate the 2024 election year, safeguarding the integrity of our democratic process is more critical than ever. While…