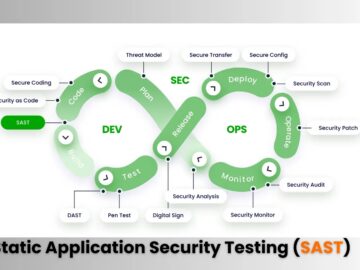
In today’s app dev world, where new apps and millions of lines of code are being deployed every day, the…
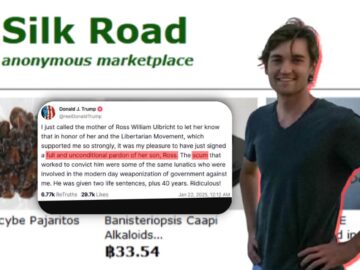
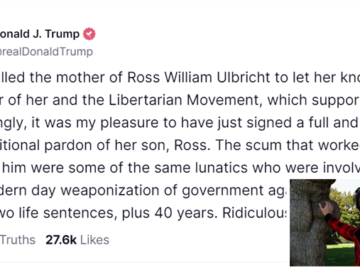
President Trump pardons Silk Road founder Ross Ulbricht, slamming prosecutors as “scum.” The move reignites debates on cybercrime justice, presidential…
Lookout announced their new Lookout Mobile Intelligence Application Programming Interfaces (APIs), exponentially expanding the scope of visibility into enterprise mobile…
Billionaire Elon Musk, who is seen as US president Donald Trump’s right-hand man, has openly criticised the new US administration’s…
Cybersecurity researchers have uncovered a new threat targeting developers using Visual Studio Code (VS Code). A malicious extension masquerading as…
Despite last week’s confirmation of and warnings about long-standing exploitation of CVE-2024-55591, a critical vulnerability affecting Fortinet Fortigate firewalls, too…
Amazon Web Services (AWS) has announced a set of best practices aimed at helping customers protect their cloud environments against…
Jan 22, 2025Ravie LakshmananDark Web / Cryptocurrency U.S. President Donald Trump on Tuesday granted a “full and unconditional pardon” to…
Warnings about power supply issues and the scarcity of suitable sites to build new server farms have led to persistent…
A former CIA analyst, Asif William Rahman, 34, pleaded guilty today to unlawfully retaining and transmitting Top Secret National Defense…
Jan 22, 2025The Hacker NewsRisk Assessment / Browser Security As GenAI tools and SaaS platforms become a staple component in…
As Australia prepares for its 2025 federal election, concerns surrounding the integrity of the electoral process have become a focal…