The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding three critical vulnerabilities that are currently being…
In recent days, Chinese-backed cyber attacks have been making headlines, with reports indicating a surge in espionage-driven cyber campaigns targeting…
The Software AG group started the new year with a slew of changes, announcing the close of the sale of…
American football team Green Bay Packers says cybercriminals stole the credit card data of over 8,500 customers after hacking its official…
The CVE® Program has announced a significant expansion of its collaboration with Thales Group to strengthen the management and assignment…
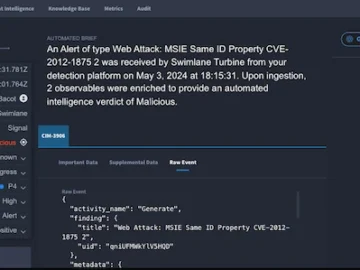
Swimlane unveiled Hero, a private agentic AI security operations (SecOps) companion. Built on the foundation of Swimlane’s Hero AI innovations,…
However, in cybersecurity, quantifying net profit becomes significantly more complex due to the intangible nature of its benefits and the…
Perhaps the defining quality of the software supply chain is complexity. Amid the countless lines of code that the modern…
SUMMARY Phishing Scam Targets PayPal: Scammers exploit PayPal’s system to link victim accounts to unauthorized addresses. Legitimate-Looking Emails: The scam…
The White House has announced the launch of the U.S. Cyber Trust Mark, a voluntary cybersecurity labeling program for consumer-grade…
APIs are the backbone of modern digital ecosystems, but their misuse can expose systems to cyber threats. Effective API throttling…
Microsoft has announced the Public Preview of Managed Identities as Federated Identity Credentials (FICs) for Microsoft Entra. The innovation aims…