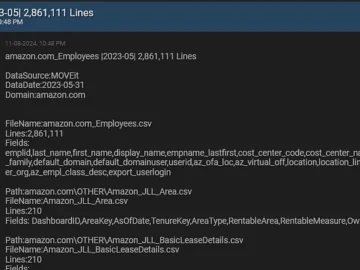
A threat actor who goes by the online moniker “Nam3L3ss” has leaked employee data belonging to a number of corporations…
VMware has announced that its popular desktop hypervisor products, VMware Workstation and VMware Fusion, are now free to all users…
The landscape of API security is evolving rapidly, driven by increasing complexities in IT environments, the proliferation of third-party APIs, and…
VMware, a leading virtualization software provider, has significantly changed its licensing model for its popular desktop hypervisor products, VMware Fusion…
In July 2024, the FBI and CISA issued warnings about increasing Distributed Denial of Service (DDoS) attacks on election infrastructure…
Thank you for joining! Access your Pro+ Content below. 12 November 2024 Innovating with weather data at the Met Office…
Dell Technologies has disclosed multiple critical security vulnerabilities in its Enterprise SONiC OS, which could allow attackers to gain control…
Apple Introduces ‘Inactivity Reboot’ Security Feature to Protect iPhones from Theft and Data Breach Apple iPhones running iOS 18.1 are…
Ahold Delhaize, one of the world’s largest grocery and eCommerce companies, is grappling with a cybersecurity breach affecting its U.S….
Dell Technologies has disclosed three critical security vulnerabilities affecting its Enterprise SONiC (Software for Open Networking in the Cloud) operating…
Ransomware attacks have become a regular fixture in the headlines, wreaking havoc across industries, leaving organizations racing to restore operations,…
The Indian Computer Emergency Response Team (CERT-In) has issued a warning about newly discovered vulnerabilities in Google Chrome that could…