UK drivers working for ride-hailing and food delivery app Bolt should be classed as staff rather than self-employed, the Employment…
Modern security tools continue to evolve, improving their ability to protect organizations from cyber threats. Despite these advances, bad actors…
TEL AVIV, Israel, November 11th, 2024, CyberNewsWire Customers can now easily integrate Sweet’s runtime detection and response platform into their…
Cybersecurity experts at Sophos are warning Australian internet users about a growing cyber threat related to a specific search term:…
By 2022, datacentres are forecast to consume about 2% of global energy. By 2026, that number is predicted to jump…
Palo Alto Networks warns of potential RCE in PAN-OS management interface Pierluigi Paganini November 08, 2024 Palo Alto Networks warns…
Halliburton has revealed that an August ransomware attack has led to $35 million in losses after the breach caused the…
Researchers discovered five malicious npm packages that target Roblox developers, spreading malware to steal credentials and personal information. These packages,…
The ongoing procurement process for NHS England’s Outcomes and Registries Platform (ORP) continues to draw concerns over the state of…
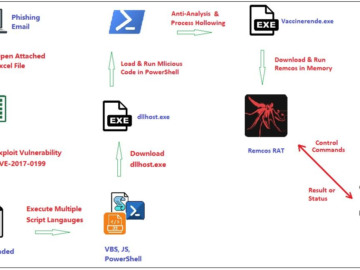
A new fileless variant of Remcos RAT observed in the wild Pierluigi Paganini November 11, 2024 Fortinet researchers discovered a…
Hackers weaponize Excel documents primarily due to their widespread use and the inherent vulnerabilities within the software. With Microsoft blocking…
Decentralized finance (DeFi) protocol DeltaPrime has fallen victim to yet another major exploit. Hackers siphoned off approximately $4.8 million worth of ARB and AVAX tokens. The…