A critical security vulnerability in Palo Alto Networks’ Expedition tool is being actively exploited by hackers. CISA urges patch –…
Cyber threats are intensifying, and cybersecurity has become critical to business operations. As security budgets grow, CEOs and boardrooms are…
NetApp has upgraded its AFF A- and C-series flash storage arrays while also boosting capacity and performance in StorageGrid object…
Cybercriminals exploit leaked credentials, obtained through various means, to compromise systems and data, enabling them to gain unauthorized access. This…
In the rapidly evolving world of digital transformation, security has become one of the most critical challenges for organizations. While…
Nov 11, 2024Ravie LakshmananVulnerability / Risk Mitigation Hewlett Packard Enterprise (HPE) has released security updates to address multiple vulnerabilities impacting…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued multiple advisories alerting the public to critical vulnerabilities affecting industrial control…
API attacks can be costly. Really costly. Obvious financial impacts like legal fines, stolen finances, and incident response budgets can…
Amid a rising tide of low-cost weaponized adversary drones menacing American troops abroad, the US military is pulling out all…
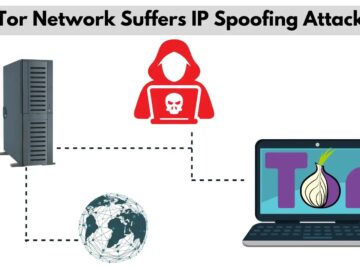
In late October 2024, a coordinated IP spoofing attack targeted the Tor network, prompting abuse complaints and temporary disruptions. While…
Elon Musk’s Starlink Satellite Broadband Caught in the Crossfire of 2024 U.S. Election Controversy Elon Musk’s Starlink, a satellite-based internet…
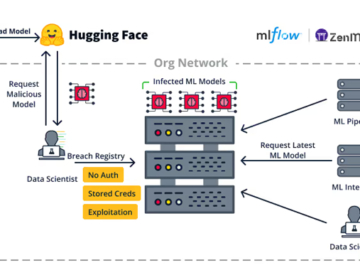
Nov 11, 2024Ravie LakshmananMachine Learning / Vulnerability Cybersecurity researchers have uncovered nearly two dozen security flaws spanning 15 different machine…