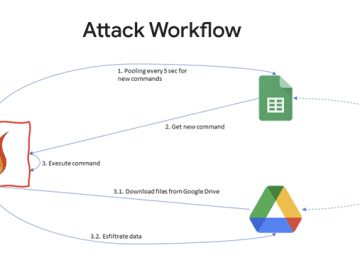
Apr 17, 2023Ravie LakshmananCyber Threat / Cloud Security A Chinese nation-state group targeted an unnamed Taiwanese media organization to deliver…
The Police Service of Northern Ireland (PSNI) and Ireland’s An Garda Síochána are probing a series of data breaches at…
Monday 21 November: With a focus to create awareness and build an unwavering cybersecurity network, infosec publication The Cyber Express…
CommScope, a globally renowned provider of advanced network solutions, has allegedly fallen prey to the notorious Vice Society ransomware group….
TL/DR: Adding to its slew of accolades, Detectify’s solution has been recognized by the G2 Summer Report 2022 as a…
An underappreciated candidate for light and fast database transactions. Update: read the HackerNews discussion. SQLite (“see-quell-lite”) is a lightweight Sequel,…
The Polish military, along with its CERT.PL recently discovered that a Russian state-sponsored group of hackers, dubbed APT29 (aka Cozy…
Law enforcement abuse of databases is far from unique to ICE agents. In the past decade, local police around the…
By Karl Pulanco, Product Portfolio Manager, Yondu Modern businesses no longer need a physical store to sell goods and services….
How to Master Nmap like a Pro: The Ultimate Guided Learning Labs! Source link
Brave Software disclosed a bug submitted by mrzheev: https://hackerone.com/reports/1884042 – Bounty: $500 Source link
Apr 17, 2023Ravie LakshmananRansomware / Cyber Attack Threat actors associated with the Vice Society ransomware gang have been observed using…