Maybe we can’t find any aliens because they couldn’t make it past the Maloch Barrier Created/Updated: April 16, 2023 Maloch…
Take some work off your plate while beefing up security with three changes you can make today. We’ve already got…
WhatsApp, owned by Facebook, has introduced three new account protection features to enhance the security and privacy of its users,…
Internet Bug Bounty disclosed a bug submitted by sw0rd1ight: https://hackerone.com/reports/1895277 – Bounty: $2400 Source link
Cloud-based security solutions have become increasingly popular in recent years, as more and more businesses are moving their operations to…
Matt Atkinson | 29 October 2021 at 12:22 UTC Burp Suite’s authenticated scanning feature enables users to scan privileged areas…
A renowned security analyst and bug hunter, Nagli (@naglinagli), recently uncovered a critical security vulnerability in ChatGPT. With just a…
Fraudsters are underestimating the power of AI to detect fake IDs, according to a new report from Ondato. Based on…
Visualizing Live Hacking Events: Hackers Break Records at H1-702 Source link
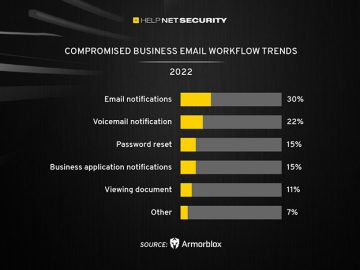
Across all BEC attacks seen over the past year, 57% relied on language as the main attack vector to get…
TL/DR: OAuth users are being urged to check their sign-in flows for third-party scripts, including error flows, that could expose…
How threat modeling and pushing left help create a stable foundation for secure software. If you’ve ever watched a kid…