Retail and e-commerce organizations are major targets this time of year, which is why proactive security testing is essential to…
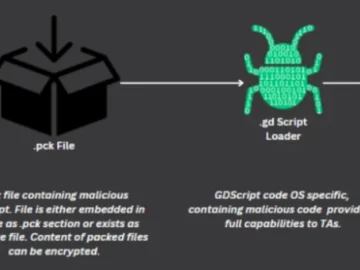
Hackers have used new GodLoader malware exploiting the capabilities of the widely used Godot game engine to evade detection and…
The Royal Automobile Club of Queensland (RACQ) has recruited Aussie Broadband CIO Anna Clive, following a mid-year leadership restructure at…
CISOs often struggle with proving ROI from security initiatives when trying to secure buy-in from the board and prioritize budget….
Threat actors are using public exploits for a critical authentication bypass flaw in ProjectSend to upload webshells and gain remote…
The Attorney-General’s Department (AGD) is looking to transform itself into a cloud-native organisation through its ongoing IT strategy. The agency…
Zello is warning customers to reset their passwords if their account was created before November 2nd in what appears to…
South East Water is on the cusp of going live with two Salesforce AI services that it hopes will allow…
The IoT Security Foundation’s fifth annual report into the state of vulnerability disclosure consumer Internet of Things, produced by Copper…
Microsoft has denied claims that it uses Microsoft 365 apps (including Word, Excel, and PowerPoint) to collect data to train…
Threat actors are using an ingenious new way for covertly delivering malware to a wide variety of operating systems and…
Originally published in Security Magazine When the pandemic hurled us into a cybersecurity crisis, there were some who held out…