GraphQL is a modern query language for Application Programming Interfaces (APIs). Supported by Facebook and the GraphQL Foundation, GraphQL grew…
Microsoft and Citizen Lab discovered commercial spyware made by an Israel-based company QuaDream used to compromise the iPhones of high-risk…
According to GDAC, stolen cryptocurrencies include 61 Bitcoins, 350.5 Ethers, 10 million of the WEMIX gaming currency, and $220,000 worth…
Recording Slides Supplemental Demo Video: Source link
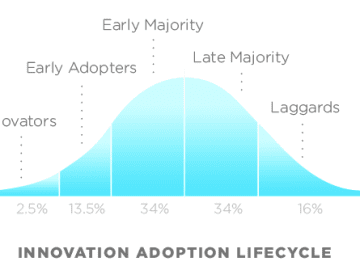
In the dynamic world of business, the ability to make data-driven decisions is essential for organizations seeking a competitive edge….
What after Recon? – Manual Hunting: Escaping the Recon Trap Source link
The Kodi Foundation has disclosed a data breach after hackers stole the organization’s MyBB forum database containing user data and…
How easy is it to tweet as anyone? | Twitter Hacks & Bug Bounty Source link
VoIP communications company 3CX confirmed today that a North Korean hacking group was behind last month’s supply chain attack. “Based…
Sophos has released a new security advisory that has fixed 3 of its significant vulnerabilities, allowing threat actors to execute…
Broken Access Control – Lab #5 URL-based access control can be circumvented | Short Version Source link
Malware developers have created a thriving market promising to add malicious Android apps to Google Play for $2,000 to $20,000,…