How They Got Hacked Episode Fifty One 51 Source link
Why I Quit My Job at Bugcrowd Source link
Less than a month ago, Twitter indirectly acknowledged that some of its source code had been leaked on the code-sharing…
요즘 장난감 삼아 Crystal과 Elixir로 여러가지 코드를 작성해보고 있습니다. 특히 Crystal은 Ruby와 제가 예전에 한번 소개하기도 헀고 Ruby와 거의 유사한…
Do you own a Tesla electric vehicle? If yes, then this news piece could be of interest to you. According…
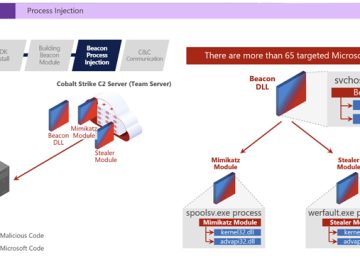
Apr 07, 2023Ravie Lakshmanan Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center (Health-ISAC) to…
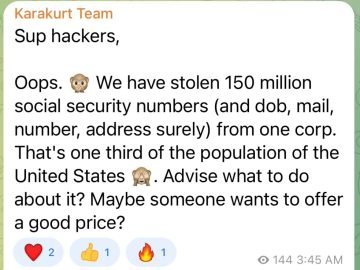
The Karakurt extortion group is back after a hiatus, claiming two victims. The data extortion group has claimed to have…
Deep Recursion Attack + Introspection | Damn Vulnerable GraphQL App | GraphQL Exploitation – Part 4 Source link
Telegram is becoming an increasingly popular platform for users as well as cyber-criminals. It has become a Mini Dark-web since…
[ This article was originally published here ] This is the first of a series of consultant-written blogs around PCI…
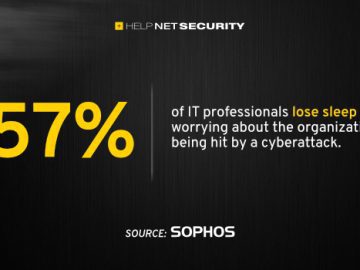
93% of organizations find the execution of some essential security operation tasks, such as threat hunting, challenging, according to Sophos….
Apr 07, 2023Ravie LakshmananIndustrial Control System The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published eight Industrial Control Systems…