People reveal more personal information when you ask them the same questions a second time – according to new research…
Fake Twitter accounts are dangerously out of control Source link
MSPs are focusing on automation and integration between their core tools to improve efficiency, service delivery and cost management, according…
LIGHTS? 60 seconds on why i think a dynamic light setup is important. Source link
GovTech’s Cyber Security Group recently organised the STACK the Flags Cybersecurity Capture-the-Flag (CTF) competition from 4th to 6th December 2020….
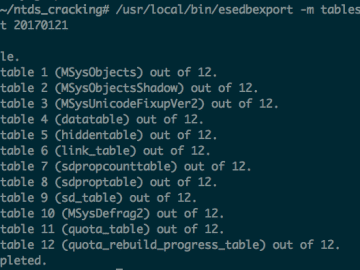
On internal pens, it’s really common for me to get access to the Domain Controller and dump password hashes for…
No BS Guide – Top 6 Browser Extensions for Bug Bounty Source link
Hacking 1Password | Episode 1 – Introduction Source link
Cloud mining is a way for you to purchase mining power from a remote data centre. Cloud mining works in…
Broken Access Control – Lab #11 Insecure direct object references | Long Version Source link
Cross-Site Scripting (XSS) Explained Source link
Experts have warned that criminals have been exploiting a vulnerability to use the CAN injection method for stealing connected cars….