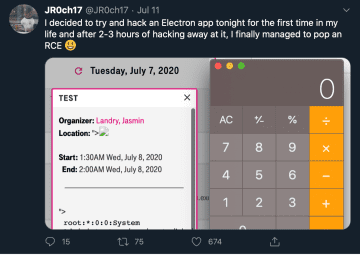
The list of people and organizations that are hungry for your location data—collected so routinely and packaged so conveniently that…
Does “Erase All Content and Settings” actually wipe user data on macOS? Source link
WHAT TO DO WHEN YOU HAVE DEFCON FOMO?? :(((( Source link
How much has Virtual reality (VR) technology evolved? It has evolved enough for indie virtual reality projects to become commonplace,…
For better or worse, Node.js has rocketed up the developer popularity charts. Thanks to frameworks like React, React Native, and…
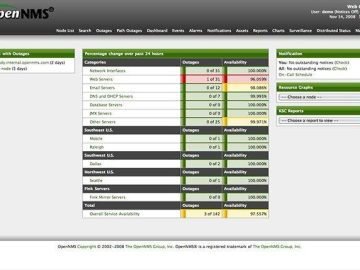
Background On my last internal penetration test, I compromised a server running OpenNMS. During post-exploitation, I recovered several password hashes…
NO BS BUG BOUNTY GUIDES – INTRO Source link
By Tyler Farrar, CISO, Exabeam According to the Exabeam State of the SIEM survey, security professionals remain confident in the…
By Timothy Liu, CTO and co-founder, Hillstone Networks In the cybersecurity world, buzzwords seem proliferate with the changing of the…
In an announcement on Telegram, the Russian KillNet hacker group claimed to have targeted NATO with DDoS attacks, stolen plain-text…
Broken Access Control – Lab #6 Method-based access control can be circumvented | Long Version Source link