Following a series of high-profile data breaches that originated via its tech, identity and access management (IAM) technology supplier Okta…
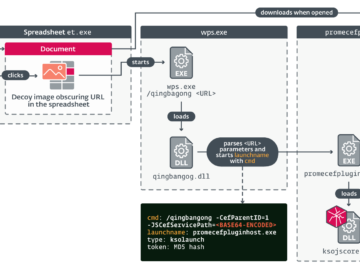
South Korea-linked group APT-C-60 exploited a WPS Office zero-day Pierluigi Paganini August 30, 2024 South Korea-linked group APT-C-60 exploited a…
Pentest reports are a requirement for many security compliance certifications (such as GDPR and HIPAA), and having regular pentest reports on hand can…
The events surrounding Pavel Durov’s arrest on 24 August 2024 due to Telegram’s suspected operational crimes worsened discussions on topics…
Iranian cyber actors have been identified as the perpetrators behind ransomware attacks targeting U.S. organizations across multiple sectors. This revelation…
A year-long malware campaign targets Roblox developers using fake NPM packages mimicking “noblox.js” to steal data. Despite takedowns, new threats…
Cary, North Carolina, August 30th, 2024, CyberNewsWire INE Security is pleased to announce that it has been recognized as a…
Aug 30, 2024Ravie LakshmananCyber Threat / Cyber Espionage Cybersecurity researchers have unearthed new network infrastructure set up by Iranian threat…
Fota Wildlife Park, one of Ireland’s premier wildlife attractions, has fallen victim to a cyberattack that has potentially compromised the…
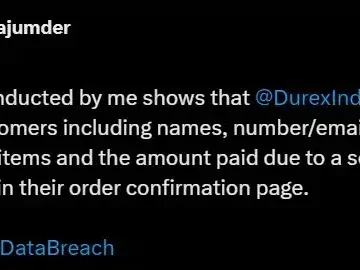
Durex India, the local arm of the popular British condom and personal lubricants brand, has reportedly suffered a significant cyberattack…
While the cloud has been the destination of choice for many, there are plenty of good reasons why organisations can’t…
Threat actors exploit Atlassian Confluence bug in cryptomining campaigns Pierluigi Paganini August 30, 2024 Threat actors are actively exploiting a…