Currently, Anthropic and OpenAI hold a kill switch that can stop the spread of potentially harmful AI agents. OpenClaw primarily…
Amazon Web Services (AWS) is pleased to announce the successful completion of Payment Card Industry Personal Identification Number (PCI PIN)…
Microsoft Defender has been investigating reports of malicious Chromium‑based browser extensions that impersonate legitimate AI assistant tools to harvest LLM…
Qualys’ Key Takeaways Qualys Named a Leader: Recognized as one of only three leaders in The Forrester Wave: Cloud-Native Application…
Control characters like SOH, STX, EOT and ETX were never meant to run your code – but in the world…
Ravie LakshmananMar 04, 2026Malware / Windows Security Cybersecurity researchers have disclosed details of an advanced persistent threat (APT) group dubbed…
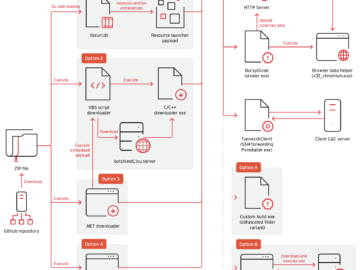
Massive GitHub malware operation spreads BoryptGrab stealer Pierluigi Paganini March 08, 2026 Trend Micro found BoryptGrab stealer spreading through 100+…
I. INTRO One of the daily tasks of Pentesters or Redteamers is to establish and maintain persistence to ensure…
Microsoft was the most targeted vendor, with 25 zero-days exploited across its products, followed by Google with 11, Apple with…
Russian-state hackers wasted no time exploiting a critical Microsoft Office vulnerability that allowed them to compromise the devices inside diplomatic,…
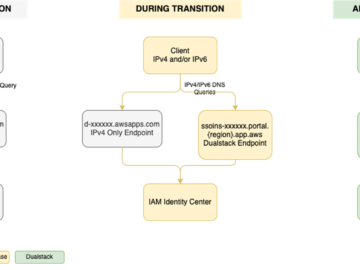
Amazon Web Services (AWS) recommends using AWS IAM Identity Center to provide your workforce access to AWS managed applications—such as…
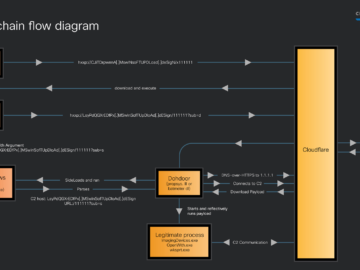
Cisco Talos discovered an ongoing malicious campaign since at least as early as December 2025 by a threat actor we track as “UAT-10027,” delivering a previously undisclosed backdoor dubbed…