An emergency security patch was released by Linux recently to fix a kernel-level security critical severity vulnerability. This vulnerability has…
Adam Bannister 14 November 2022 at 16:16 UTC Updated: 24 November 2022 at 12:50 UTC AppSec engineer keynote says Log4j…
[ This article was originally published here ] SEATTLE–()–®, an internationally recognized leader in network measurement and connectivity intelligence, commends…
Regula has presented their vision of the developments that will shape the industry’s landscape in 2023. Deepfakes, new cyber-hygiene norms,…
Jessica Haworth 15 November 2022 at 15:39 UTC Updated: 15 November 2022 at 15:47 UTC Patched bug could have leaked…
by Gary S. Miliefsky, Publisher of Cyber Defense Magazine As we saw with major holidays including Black Friday and Cyber…
Cyberattacks in the cloud are often overlooked and increasingly important By Bence Jendruszak, Co-Founder and COO, SEON Most businesses today…
[ This article was originally published here ] SANTA CLARA, Calif.–()–, a leading provider of innovative and accessible cybersecurity solutions,…
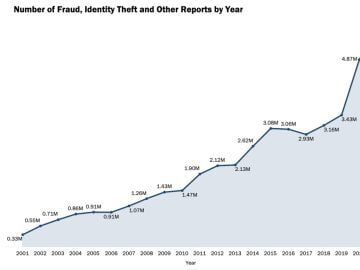
The third quarter of 2022, APWG observed 1,270,883 total phishing attacks — is the worst quarter for phishing that APWG…
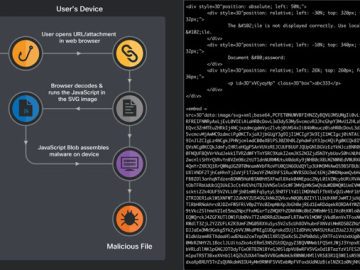
Dec 15, 2022Ravie LakshmananEmail Security / Endpoint Security Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG)…
John Leyden 15 November 2022 at 16:10 UTC Updated: 16 November 2022 at 11:18 UTC Patched SQLi and logical access…
By Dan Richings, Senior Vice President Product Management, Adaptiva The average enterprise organization has thousands of endpoint devices, ranging from…