[ This article was originally published here ] SANTA CLARA, Calif.–()–, a leading provider of innovative and accessible cybersecurity solutions,…
The third quarter of 2022, APWG observed 1,270,883 total phishing attacks — is the worst quarter for phishing that APWG…
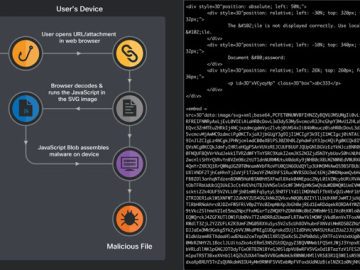
Dec 15, 2022Ravie LakshmananEmail Security / Endpoint Security Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG)…
John Leyden 15 November 2022 at 16:10 UTC Updated: 16 November 2022 at 11:18 UTC Patched SQLi and logical access…
By Dan Richings, Senior Vice President Product Management, Adaptiva The average enterprise organization has thousands of endpoint devices, ranging from…
Well-implemented fraud prevention measures can ensure your business thrives today and is future proof for tomorrow. By Patrick Kelly, Americas…
Dec 15, 2022Ravie LakshmananCyber Attack / DDoS-for-Hire The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48…
Adam Bannister 16 November 2022 at 15:02 UTC Updated: 16 November 2022 at 15:06 UTC Widespread exploitation deemed ‘unlikely’ given…
By Zac Amos, Features Editor, ReHack Businesses must leverage various types of information as the world becomes increasingly digital and…
By Randy Reiter CEO of Don’t Be Breached There were many massive Data Breaches in 2022. Don’t be a member…
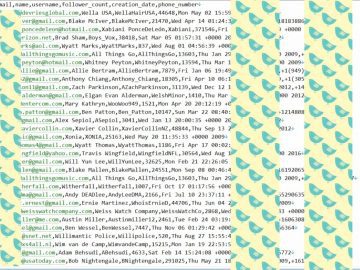
The sample data seen by Hackread.com shows that the sold information also includes records on top celebrities and political figures,…
Dec 15, 2022Ravie Lakshmanan NuGet, PyPi, and npm ecosystems are the target of a new campaign that has resulted in…