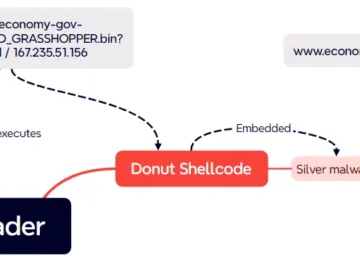
A recent cybersecurity investigation has uncovered a sophisticated operation known as “Supposed Grasshopper,” targeting both Israeli government entities and private…
The Harry Perkins Institute of Medical Research, one of Australia’s leading medical research institutes, has reportedly suffered a cyberattack carried…
Axis Finance Limited, a prominent non-banking financial company, has announced a strategic leadership appointment that is set to strengthen its…
Polish government investigates Russia-linked cyberattack on state news agency Pierluigi Paganini July 03, 2024 The Polish government is investigating a…
Cybercriminals have intensified their efforts to exploit Apple ID users through a new wave of malicious SMS campaigns. These phishing…
Regula has released a significant update to its operating software, Regula Forensic Studio. This major revamp enhances the functionality of…
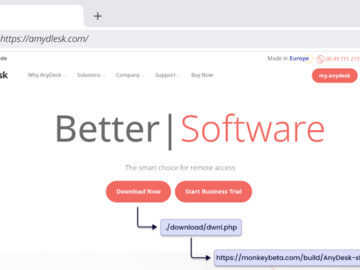
Jul 03, 2024NewsroomMalware / SEO Poisoning The loader-as-a-service (LaaS) known as FakeBat has become one of the most widespread loader…
Microsoft has discovered and disclosed two significant vulnerabilities in Rockwell Automation’s PanelView Plus devices. These vulnerabilities could be remotely exploited…
The DDoS attacks have evolved tremendously since 2016, with Mirai-like botnets setting new records. Attack frequency and intensity increased notably…
UK-based law firm Barings has brought to light a concerning incident involving alleged cyber espionage targeting British armed personnel. According…
Splunk is a software platform designed to search, analyze, and visualize machine-generated data from various sources, including websites, applications, sensors,…
In today’s interconnected digital landscape, ransomware has emerged as one of the most pervasive and damaging cyber threats. These malicious…