Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim…
A recent scoop by Reuters revealed that mobile apps for the U.S. Army and the Centers for Disease Control and Prevention…
“It is not very good at detecting weak jammers or jammers on other frequencies,” Walter explains, adding that an aircraft’s…
For reasons of safety, computers that are separated by an air gap are not connected to the Internet or any…
SMB servers that have ksmbd enabled are vulnerable to hacking due to a major Linux kernel vulnerability (CVSS score of…
Shadow APIs (Application Programming Interfaces) are now the biggest threat facing API security today. Analysis of more than 20 billion…
[ This article was originally published here ] SAN DIEGO–()–Triden Group Corp announced today that it has achieved SOC 2…
Dec 24, 2022Ravie LakshmananSoftware Security / Supply Chain Threat actors have published yet another round of malicious packages to Python…
S768.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have…
John Leyden 16 December 2022 at 17:43 UTC Updated: 19 December 2022 at 14:19 UTC Your fortnightly rundown of AppSec…
Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim…
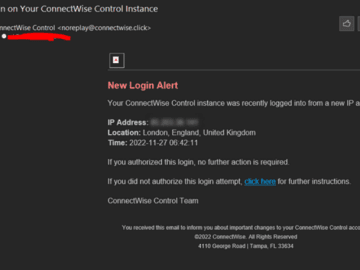
ConnectWise, which offers a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning…