Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim…
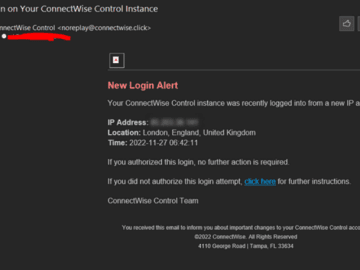
ConnectWise, which offers a self-hosted, remote desktop software application that is widely used by Managed Service Providers (MSPs), is warning…
Meta says it applies the concepts of “adversarial design” to build systems with the assumption that attackers will try to…
On December 6th, 2022, CloudSEK announced that the firm had been the target of a cyber attack. The internal investigation…
Strong IGA as a strong foundation for Zero Trust Architecture A colleague and I recently had a discussion of Zero…
A few days ago, Comcast hit the news headlines for increasing its service price so much that many of its…
As we are nearing the end of 2022, looking at the most concerning threats of this turbulent year in terms…
UCSERVICE.EXE Information This is an undesirable program. This file has been identified as a program that is undesirable to have…
Prizes offered to anyone who can bypass the library and capture the flag A new open source library designed to…
Organised by Eskenzi PR in media partnership with the IT Security Guru, the Most Inspiring Women in Cyber Awards aim…
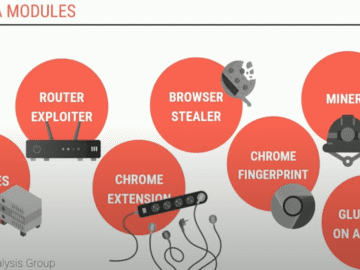
In December 2021, Google filed a civil lawsuit against two Russian men thought to be responsible for operating Glupteba, one…
As Russia’s invasion of Ukraine drags on, navigation system monitors reported this week that they’ve detected a rise in GPS…