A novel malware known as Volcano Demon has been observed targeting Windows workstations and servers, obtaining administrative credentials from the…
Vintage Investment Partners, a global venture capital platform managing $4 billion in assets, has announced the appointment of Ilan Leiferman…
A critical security vulnerability has been identified in OpenStack, a widely used open-source cloud computing platform. The flaw tracked as…
Yet Google and its hardware partners argue privacy and security are a major focus of the Android AI approach. VP…
Pakistan-linked Transparent Tribe (aka APT 36, Operation C-Major) disguises CapraRAT, an Android spyware, as popular apps to steal your data….
Enterprise Resource Planning (ERP) system eViridis has reportedly suffered a significant data breach, potentially impacting its clients as well. A…
Brazil data protection authority bans Meta from training AI models with data originating in the country Pierluigi Paganini July 04,…
Jul 04, 2024NewsroomVulnerability / Critical Infrastructure Microsoft has revealed two security flaws in Rockwell Automation PanelView Plus that could be…
Linux servers often provide hosting for critical applications, websites, and databases, which makes them a lucrative target for intruders to…
Amazon Web Services (AWS) has announced a $2 billion strategic partnership with the Australian Government to create a “Top Secret”…
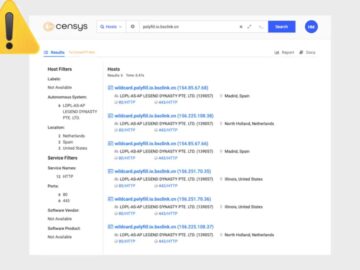
Over 380,000 web hosts have been found embedding a compromised Polyfill.io JavaScript script, linking to a malicious domain. This supply…
The People’s Cyber Army, associated with APT44, and NoName057 allegedly orchestrated a series of DDoS attack on Denmark. These attacks…