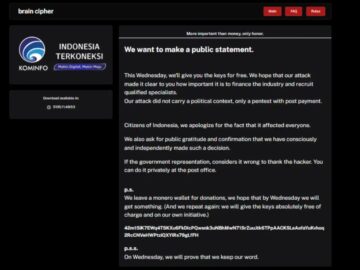
The notorious hacking group Brain Cipher has released decryption keys for free, allowing victims to recover their encrypted data without…
Jul 02, 2024NewsroomDigital Regulation / Tech News Meta’s decision to offer an ad-free subscription in the European Union (E.U.) has…
Affirm Holdings, a prominent U.S. financial technology firm, announced that the personal information of Affirm card users may have been…
Did a threat actor lie about orchestrating a data breach containing sensitive data about 8,000 students and faculty of a university…
Australia’s leading financial institutions are bracing for what could be the most significant cyber attack in the history of the…
In this Help Net Security interview, Lingping Gao, CEO at NetBrain, discusses the challenges NetOps teams face in maintaining production…
Jul 02, 2024NewsroomData Theft / Wi-Fi Security An Australian man has been charged with running a fake Wi-Fi access point…
As a security professional, it can be tempting to believe that with sufficient resources we can achieve of state of…
Pipeline Will Support Company’s Highly Proactive Buy & Build Business Model Cyber A.I. Group, Inc., an emerging growth global cybersecurity,…
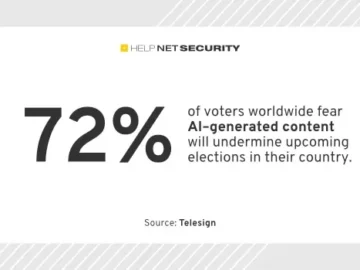
As the volume of digital business rises year over year, the potential for AI-enhanced digital fraud increases with it, according…
A critical vulnerability in the Command Line Interface (CLI) of Cisco NX-OS Software is currently under active exploitation, allowing attackers…
A data breach at insurance giant Prudential has ballooned far beyond initial estimates, with regulators informed that over 2.5 million…