The hacker group known as TransparentTribe, also referred to as APT-36, has intensified its cyber espionage activities.
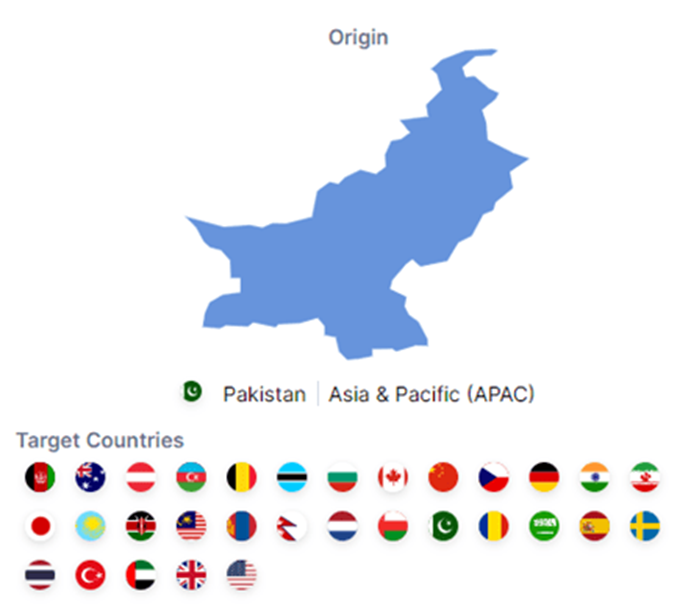
This group, originating from Pakistan, has been actively targeting Indian government organizations, military personnel, and defense contractors with sophisticated cyberattacks aimed at compromising security and gathering sensitive information.
TransparentTribe mostly goes after India and Afghanistan, but it has also been seen going after Australia, Austria, Azerbaijan, Belgium, Botswana, Bulgaria, Canada, China, Czech, Germany, Iran, Japan, Kazakhstan, Kenya, Malaysia, Nepal, the Netherlands, Oman, Pakistan, Romania, Saudi Arabia, Spain, Sweden, Thailand, Turkey, the UAE, the UK, and the USA.
Free Webinar | Mastering WAAP/WAF ROI Analysis | Book Your Spot
Overview of TransparentTribe’s Operations
TransparentTribe is notorious for its well-orchestrated attacks on various platforms, including Windows, Android, and Linux.
The group employs various tactics, such as creating fake websites and documents that mimic legitimate government entities. This deceives targeted users into disclosing their credentials or downloading malware.

One of the primary methods TransparentTribe uses involves exploiting vulnerabilities within systems to deploy malware and conduct surveillance.
The group has been documented using several critical vulnerabilities outlined below.
This vulnerability lies in the MSCOMCTL.OCX component of Microsoft systems, allowing remote code execution.
TransparentTribe has crafted malicious files that exploit this vulnerability to execute arbitrary code on the victim’s machine, leading to unauthorized access and control.
Another significant vulnerability targeted by TransparentTribe is CVE-2010-3333, a stack-based buffer overflow issue in Microsoft Office.
This flaw can be exploited through specially crafted documents, enabling attackers to execute code under the guise of the logged-in user.
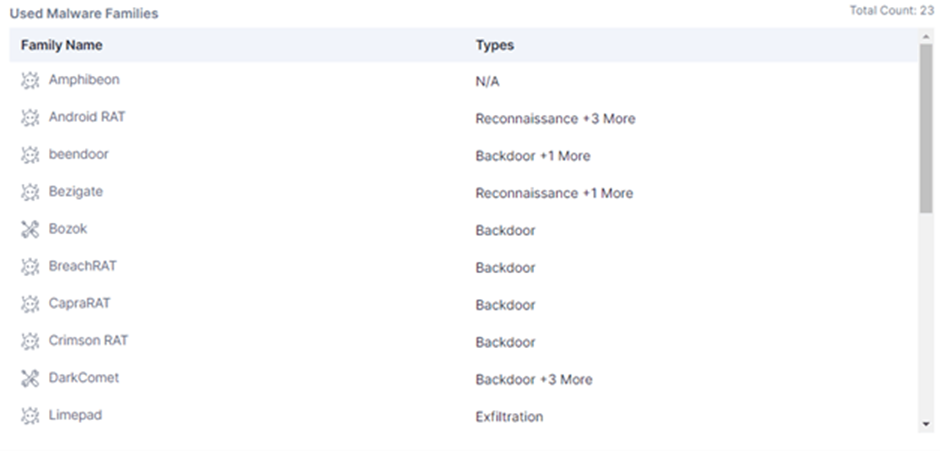
TransparentTribe utilizes a diverse arsenal of tools to infiltrate and persist within the targeted systems.
These include various Remote Access Trojans (RATs), such as Crimson RAT, DarkComet, and ObliqueRAT, which allow remote control of compromised systems.
The group’s strategy often involves initial infection through phishing emails, malicious advertisements (malvertising), and social engineering tactics.
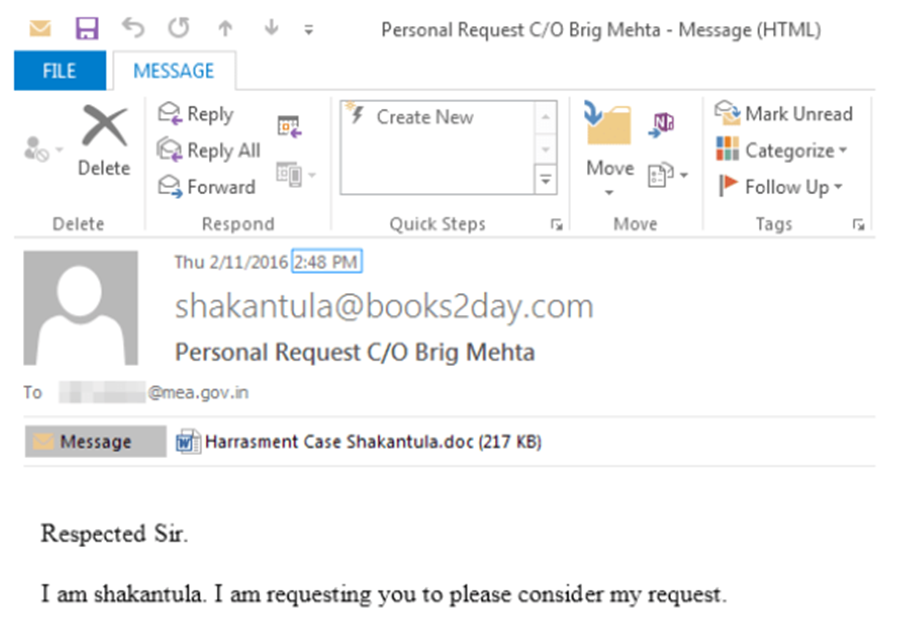
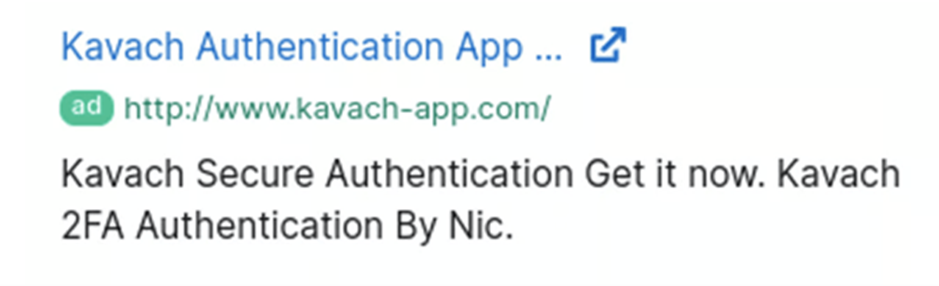
The group has been observed using domains with typo-squatted names to mimic official websites, which are then used to host malicious files.
Additionally, TransparentTribe leverages social engineering, notably through platforms like YouTube, where they create fake profiles to lure individuals into downloading malicious applications.
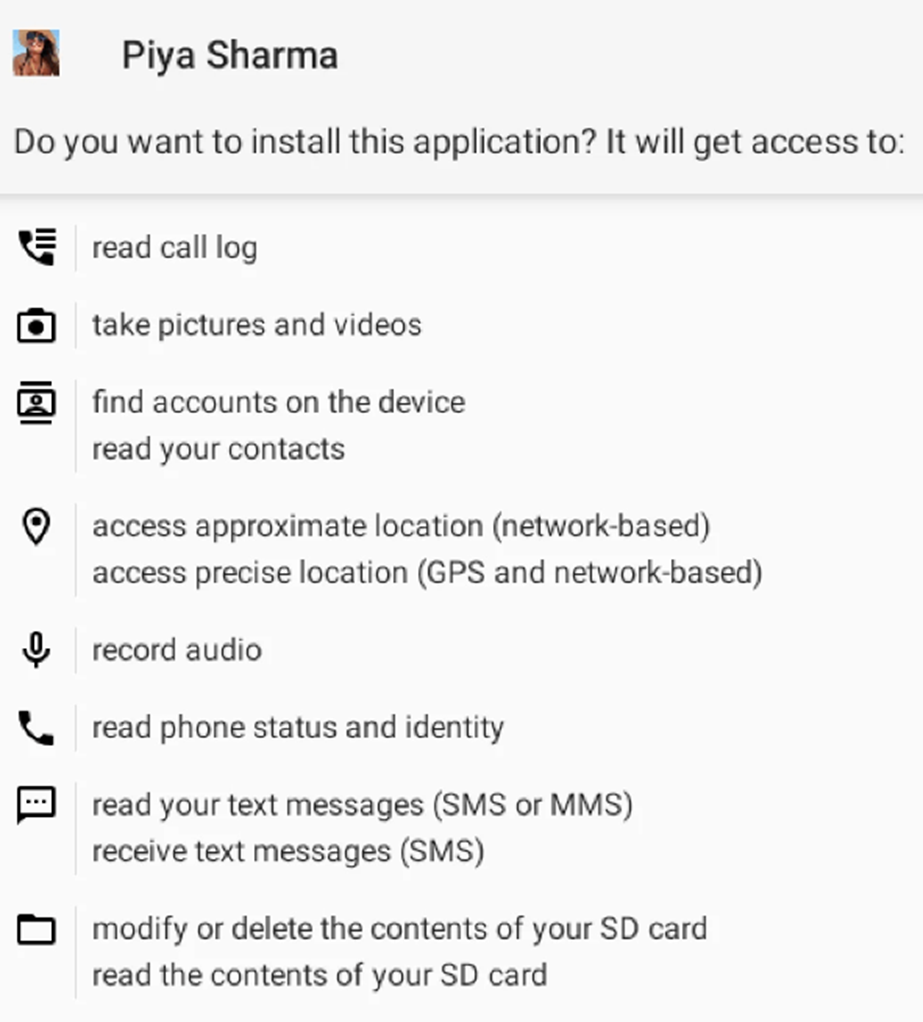
The activities of TransparentTribe highlight a significant threat to national security for India and other targeted nations.
The group’s continuous evolution of tactics and sophisticated tools necessitates a robust cybersecurity posture and awareness among potential targets.
Organizations are urged to implement stringent security measures, regular updates, and employee training to mitigate the risks of such advanced persistent threats.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP