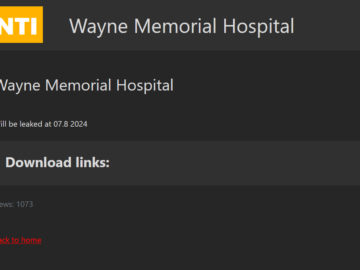
Monti gang claims the hack of the Wayne Memorial Hospital in Pennsylvania Pierluigi Paganini July 01, 2024 Wayne Memorial Hospital…
On July 20, the United States Commerce Department will ban new sales of popular antivirus software made by Moscow-based Kaspersky…
CISA, in collaboration with the Fauquier County Sheriff’s Office, the Fauquier County Fire Rescue System, and Fauquier County Public Schools,…
A malware campaign of huge magnitude, and perhaps run by just one group, is using artificially nested files for distribution…
Niconico, the Japanese video-sharing website, and its parent company KADOKAWA Inc. have provided crucial updates regarding the significant cyberattack they…
BleepingComputer has verified that the helpdesk portal of a router maker is currently sending MetaMask phishing emails in response to newly…
Researchers identified a new variant of credit card skimming attack, the Caesar Cipher Skimmer, targeting multiple content management systems (CMS),…
Microsoft has issued a new alert to its users, updating them on the continued threat posed by Midnight Blizzard, a…
It’s been almost two weeks since the CDK Global cyberattack paralyzed the US automotive industry and many car sales outlets…
A 42-year-old West Australian man is set to appear in Perth Magistrates Court today, facing nine charges for alleged cybercrime…
Hackers abuse Mac Stealer to covertly extract sensitive information such as passwords, financial data, and personal files from macOS devices….
Juniper Networks fixed a critical authentication bypass flaw in some of its routers Pierluigi Paganini July 01, 2024 Juniper Networks…