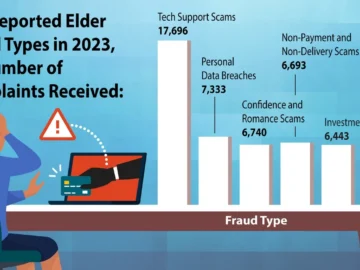
More than two dozen countries have committed to developing shared risk thresholds for frontier artificial intelligence (AI) models to limit their…
A Georgia man was sentenced to 10 years in prison after being convicted of money laundering and conspiracy in connection…
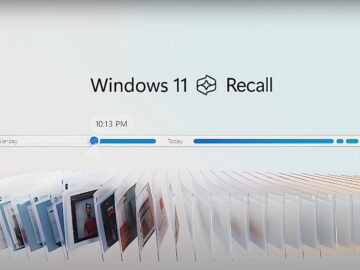
Microsoft’s announcement of the new AI-powered Windows 11 Recall feature has sparked a lot of concern, with many thinking that…
Researchers discovered REF4578, an intrusion set that uses vulnerable drivers to disable established security solutions (EDRs) for crypto mining and…
Hackers exploit ransomware as it enables them to extort money from victims by encrypting their data and demanding a ransom…
Google has embarked on an unprecedented move, revealing cybersecurity vulnerabilities of its competitor to the United States government in a…
Cybersecurity researchers have disclosed details of a previously undocumented threat group called Unfading Sea Haze that’s believed to have been…
In this podcast, we look at the impact of artificial intelligence (AI) processing on data storage with Shawn Rosemarin, vice-president…
El Centro Del Barrio, operating as CentroMed, an integrated primary care clinic, confirms a recent cyberattack marking its second breach…
AI SPERA, a leader in Cyber Threat Intelligence (CTI) solutions, announced today that its proprietary search engine, Criminal IP, is…
By Nissim Ben-Saadon, Director of Innovation, CYREBRO In today’s digital era, the healthcare industry stands at the forefront of technological…
Kelp DAO, a liquid restaking platform, today announced the closure of a $9 million private sale round, a milestone in…