John Leyden 15 November 2022 at 16:10 UTC Updated: 16 November 2022 at 11:18 UTC Patched SQLi and logical access…
By Dan Richings, Senior Vice President Product Management, Adaptiva The average enterprise organization has thousands of endpoint devices, ranging from…
Well-implemented fraud prevention measures can ensure your business thrives today and is future proof for tomorrow. By Patrick Kelly, Americas…
Dec 15, 2022Ravie LakshmananCyber Attack / DDoS-for-Hire The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48…
Adam Bannister 16 November 2022 at 15:02 UTC Updated: 16 November 2022 at 15:06 UTC Widespread exploitation deemed ‘unlikely’ given…
By Zac Amos, Features Editor, ReHack Businesses must leverage various types of information as the world becomes increasingly digital and…
By Randy Reiter CEO of Don’t Be Breached There were many massive Data Breaches in 2022. Don’t be a member…
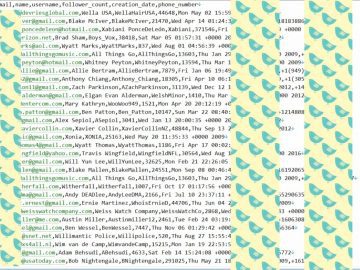
The sample data seen by Hackread.com shows that the sold information also includes records on top celebrities and political figures,…
Dec 15, 2022Ravie Lakshmanan NuGet, PyPi, and npm ecosystems are the target of a new campaign that has resulted in…
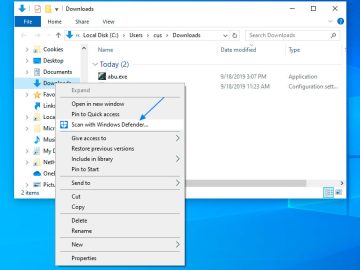
How to Use Windows Defender to Scan a Folder for Malware Windows 10 comes with a free built-in antivirus program…
Ben Dickson 17 November 2022 at 13:16 UTC Updated: 17 November 2022 at 14:10 UTC A case study on the…
Web applications, often in the form of Software as a Service (SaaS), are now the cornerstone for businesses all over…