Just as surfing the web is better with a stable internet connection, completing tasks like web scraping or bulk purchasing…
Cybercriminals are targeting Mac users interested in cryptocurrency opportunities with fake calendar invites. During the attacks the criminals will send…
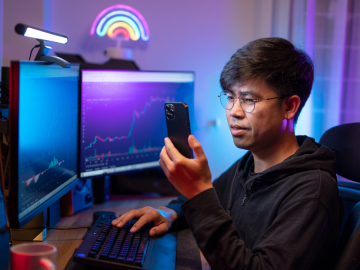
So far, the CryptoChameleon phishing scam has successfully phished over 100 victims, with many still active. Lookout has discovered a…
Microsoft has pulled the Microsoft Edge 122.0.2365.63 update after users reported receiving “Out of memory” errors when browsing the web…
The Düsseldorf Police in Germany have seized Crimemarket, the largest German-speaking illicit trading platform on the internet, arresting six people, including…
Reserve Bank of India (RBI) has warned against the dangers of “juice jacking,” a cyberattack targeting mobile users who charge…
In case you missed it, we recently introduced message templates! In our ongoing effort to improve your experience and productivity,…
Microsoft has fixed an issue causing some Microsoft 365 users’ Outlook desktop clients to stop connecting to email servers via…
The cybersecurity community has recently identified a new threat known as Phemedrone Stealer, a sophisticated malware that exploits a vulnerability…
Scheduled to take place from July to August this year in Paris, France, the 2024 Summer Olympics are set to…
At the end of 2023 and into 2024, a series of vulnerabilities in Ivanti Policy Secure network access control (NAC),…
The U.S. Department of Justice (DoJ) has unveiled an indictment against Alireza Shafie Nasab, a 39-year-old Iranian national, for his…