Pikabot is a loader malware that is active in spam campaigns and has been used by the threat group Water…
In the age of digital inter-connectedness, social media has become an integral part of our daily lives, enabling us to…
Cryptocurrency markets fluctuated wildly on the evening of Monday 9 January after the US financial regulator, the Securities and Exchange…
In a continuing saga of cyber tensions, the Maldivian Juvenile Court website appears to be the latest target, following recent…
Entire population of Brazil possibly exposed in massive data leak Pierluigi Paganini January 10, 2024 The private data of hundreds…
After gaining control of the SEC’s account, hackers posted tweets claiming that the agency had approved the listing and trading…
Jan 10, 2024NewsroomPrivacy / Regulatory Compliance The U.S. Federal Trade Commission (FTC) on Tuesday prohibited data broker Outlogic, which was…
Scotland risks “sleepwalking” into a surveillance state that places every citizen in a permanent digital line-up if it does not…
The NoName ransomware group, suspected to have Russian affiliations, has reportedly intensified its cyberattack on Finland. The recent wave of…
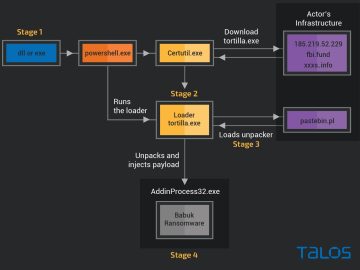
Decryptor for Tortilla variant of Babuk ransomware released Pierluigi Paganini January 10, 2024 Researchers and the Dutch Police released a…
Researchers uncovered a critical authentication bypass zero-day flaw tracked as CVE-2023-51467, with a CVSS score of 9.8 affecting Apache OFBiz’s…
Hackers use YouTube channels to deliver malware due to the huge user base of the platform. By using YouTube channels,…