The supply chain attack targeting 3CX was the result of a prior supply chain compromise associated with a different company,…
The UK’s National Cyber Security Centre (NCSC), working alongside its counterparts from Australia, Canada, New Zealand and the US, has…
As the world becomes increasingly digital, technology is at the heart of how businesses operate. How often have you heard…
Many organizations use bug bounty programs to help them protect their ever-expanding attack surface and achieve attack resistance. Bug bounties,…
ESET researchers have recently discovered that Linux users targeted with malware in the new “Operation DreamJob” Lazarus campaign for the…
The early findings of a pioneering cyber security project are showing promising signs that a novel technological approach implemented in…
Detectify Crowdsource hacker Sebastian Neef, otherwise known as Gehaxelt, has an inspirational background in ethical hacking. Driven by curiosity, a…
A recent report from CISA (US Cybersecurity and Infrastructure Security Agency) revealed that the APT 28 group was responsible for…
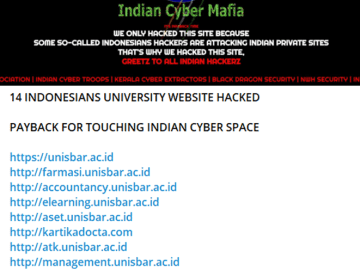
A new group of hackers, which calls itself the ‘Indian Cyber Mafia’, has allegedly launched cyberattacks on Indonesian universities. This…
Detectify collaborates with Crowdsource, our private network of ethical hackers to help our customers access the latest critical security research…
Websites of multiple U.S. universities are serving Fortnite and ‘gift card’ spam. Researchers observed Wiki and documentation pages being hosted by universities including Stanford, MIT, Berkeley,…
A hacker group known as ShadowHacker has claimed to have gained access to the database of freshersworld.com, a popular website…