An operator known as GhostSocks advertised a novel Malware-as-a-Service (MaaS) on the Russian cybercrime forum XSS.is on October 15, 2023,…
Quick Summary: AI agents enable security teams to surge ahead of the most advanced threats using automated decision-making, real time response, and…
In a recent wave of targeted phishing campaigns, the Cavalry Werewolf cluster has escalated its operations by impersonating government officials…
ProSpy, ToSpy malware pose as Signal and ToTok to steal data in UAE Pierluigi Paganini October 03, 2025 Researchers uncovered…
An extortion group has launched a new data leak site to publicly extort dozens of companies impacted by a wave of…
AmCache plays a vital role in identifying malicious activities in Windows systems. This tool allows the identification of both benign…
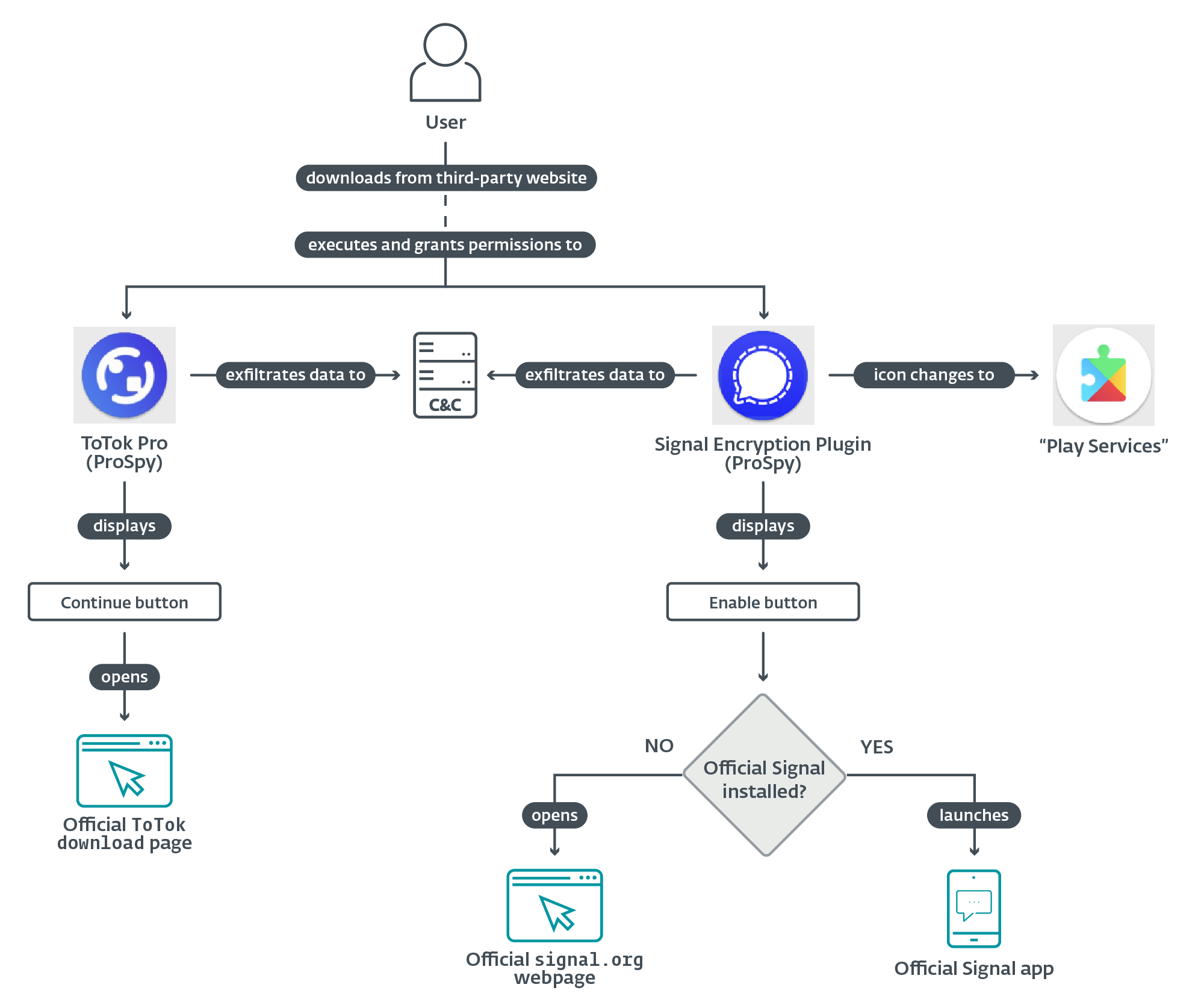
ESET researchers have uncovered two sophisticated Android spyware campaigns that target users seeking secure communication platforms by impersonating popular messaging…
SecurityWeek’s cybersecurity news roundup provides a concise compilation of noteworthy stories that might have slipped under the radar. We provide…
In recent months, a sophisticated campaign dubbed Cavalry Werewolf has emerged, targeting government and critical infrastructure organizations across Russia and…
In today’s interconnected digital landscape, businesses are more dependent than ever on third-party vendors and partners. While these relationships bring…
United States immigration authorities are moving to dramatically expand their social media surveillance, with plans to hire nearly 30 contractors…
As a cybersecurity expert who presents on TV and at security conferences regularly, Scott Schober has seen an alarmingly disproportionate…