Google is working to resolve authentication issues affecting some ChromeOS devices, which are preventing affected users from signing into their Clever…
Cisco has issued a High-severity security advisory alerting customers to a critical vulnerability in the Intermediate System-to-Intermediate System (IS-IS) feature…
The State of Nevada became the target of a significant cyberattack which resulted in a substantial network security incident impacting…
SECURITY | AI | PURPOSEUNSUPERVISED LEARNING is a newsletter about upgrading to thrive in a world full of AI. It’s…
The FBI and the Dutch Police have shut down the VerifTools marketplace for fraudulent identity documents after seizing servers in Amsterdam…
A significant cyberattack disrupted Nevada’s state government network on August 24, forcing all state office branches to shut down operations…
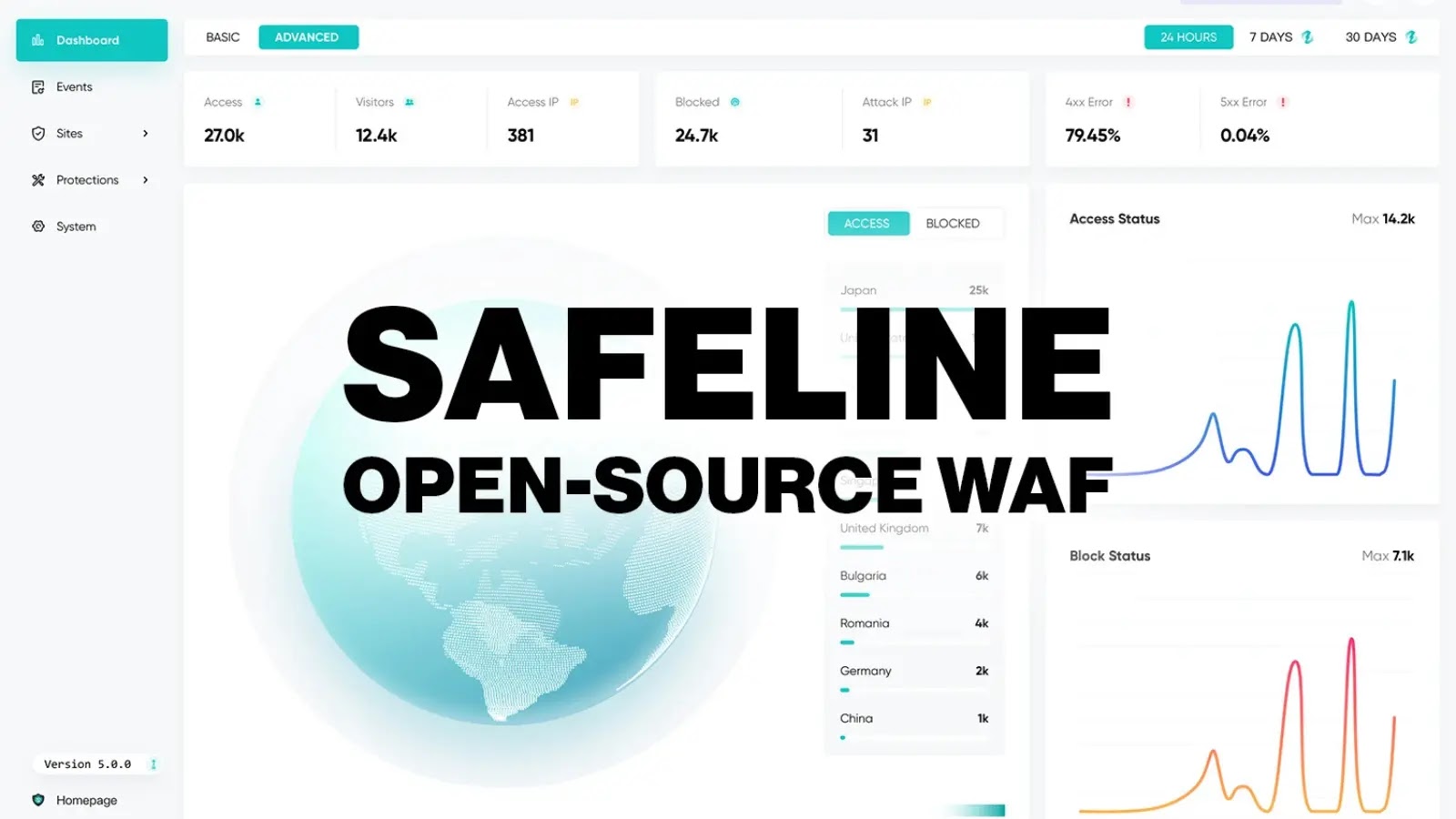
When web application protection is no longer a million-dollar luxury, and when every developer can build their own security perimeter…
Aug 28, 2025Ravie LakshmananMalware / Ransomware Cybersecurity researchers have discovered a loophole in the Visual Studio Code Marketplace that allows…
Ollama > is one of my favorite ways to experiment with local AI models. It’s a CLI that also runs…
Anthropic’s Claude Code large language model has been abused by threat actors who used it in data extortion campaigns and…
Microsoft’s recent patch for the BadSuccessor vulnerability (CVE-2025-53779) has successfully closed the direct privilege escalation path, but security researchers warn…
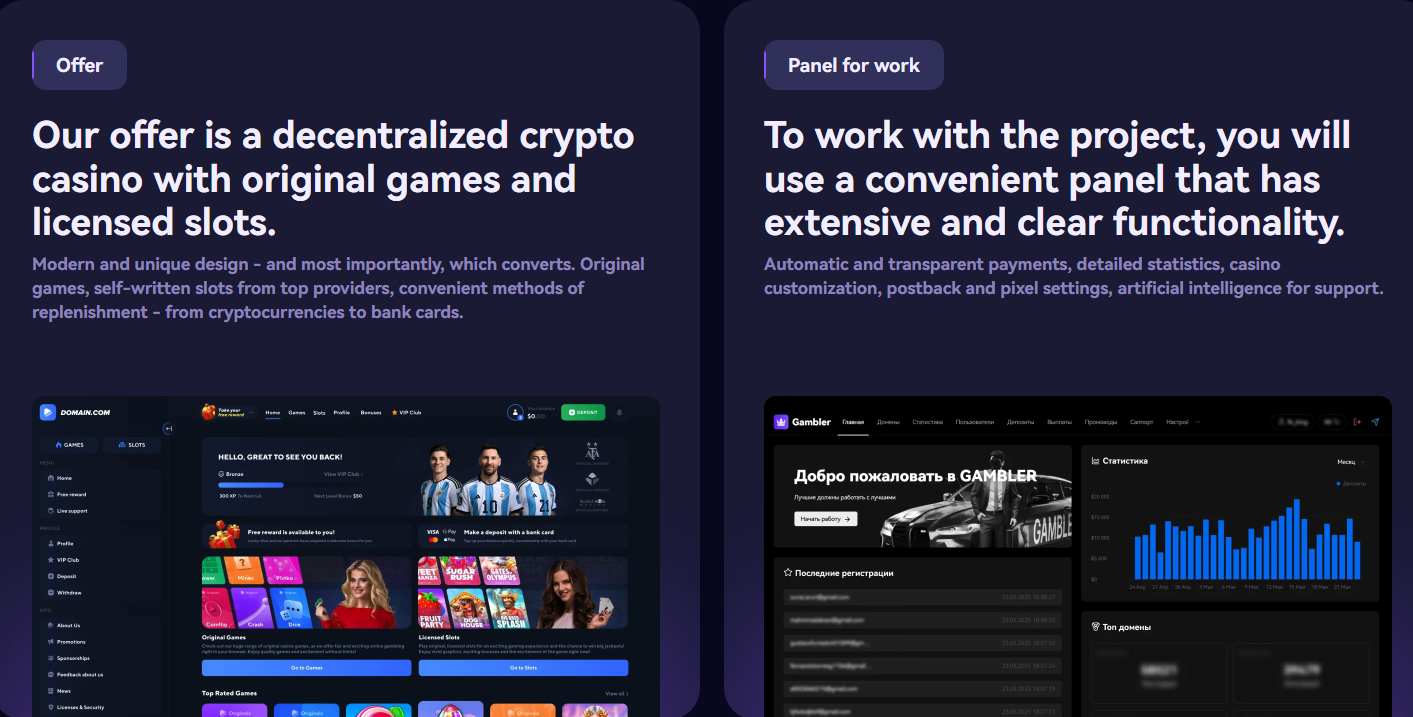
Last month, KrebsOnSecurity tracked the sudden emergence of hundreds of polished online gaming and wagering websites that lure people with…