A Proof-of-Concept (PoC) has been released for a significant vulnerability discovered in SolarWinds Web Help Desk, exposing encrypted passwords and other sensitive data.
This vulnerability arises from the predictable encryption keys used in the application and the misuse of AES-GCM encryption, a widely respected cryptographic standard.
The issue highlights the importance of secure key management and proper encryption practices in software development.
AES-GCM (Galois/Counter Mode) is an authenticated encryption mode that provides both confidentiality and integrity. However, it requires unique nonces (initialization vectors) for each encryption operation.
If the same key and nonce are reused, an attacker can exploit this to recover the encryption keystream and decrypt other ciphertexts without knowing the key.
Vulnerability in SolarWinds Web Help Desk
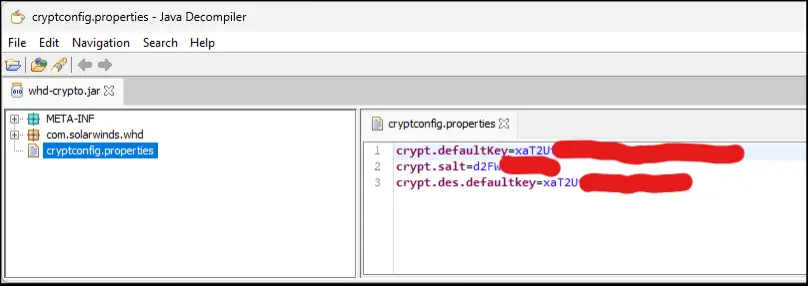
As per the NetSPI report, the vulnerability affects Web Help Desk users who utilize AES-GCM encryption for securing sensitive data such as database connection passwords, LDAP query passwords, and SMTP email passwords. The issue is twofold:
- Predicable Encryption Keys: The encryption keys used by Web Help Desk are relatively easy to recover. The default key is embedded in the application’s source code and can be accessed by decompiling the software. Additional keys are derived from database data and source code, but these transformations offer little security due to a small key space.
- Reuse of Key and Nonce: The application often reuses keys and nonces across multiple encryption operations. This misuse of AES-GCM allows attackers to recover the keystream through known plaintext attacks, enabling them to decrypt any ciphertext encrypted with the same key and nonce.
Exploitation Example
In one case, a known ciphertext and plaintext pair were used to compute the keystream via XOR.
This keystream was then applied to an unknown ciphertext to retrieve its plaintext, demonstrating how easily an attacker can exploit this vulnerability.
# Simplified Python code to demonstrate keystream recovery and decryption
def xor_keystream(plaintext, ciphertext):
keystream = bytearray()
for p, c in zip(plaintext, ciphertext):
keystream.append(p ^ c)
return keystream
# Known plaintext and ciphertext pair
known_plaintext = b'x00x00x00x09Password1'
known_ciphertext = b'frcLMeS3nchpg_Ucxz-evzlfNUlfHLnpvKyjAYisVLmlEtyZ2ZFRRiVw7Kd5KQbR'
keystream = xor_keystream(known_plaintext, known_ciphertext)
# Use keystream to decrypt unknown ciphertext
unknown_ciphertext = b'your_unknown_ciphertext_here'
unknown_plaintext = bytearray()
for uc, ks in zip(unknown_ciphertext, keystream):
unknown_plaintext.append(uc ^ ks)
print("Unknown Plaintext:", unknown_plaintext.decode('utf-8'))Recommendations and Impact
To mitigate this vulnerability, it is crucial for users to upgrade their Web Help Desk software to the latest version.
Moreover, backup files containing sensitive data should be secured with access restricted to only necessary personnel.
The discovery of this vulnerability highlights the need for robust key management practices and adherence to encryption standards in software development.
In conclusion, the release of the PoC for the SolarWinds Web Help Desk vulnerability serves as a reminder of the importance of secure coding practices and responsible disclosure of vulnerabilities.
As software continues to play a central role in managing sensitive data, ensuring that encryption is implemented correctly will become increasingly critical to protecting user privacy and preventing data breaches.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.




