Everyone values privacy, especially online. But every once in a while, a tool surfaces that completely shatters that illusion. That’s exactly what Proxyearth does. This website, along with its connected Telegram bot, claims to pinpoint the exact location of any Indian citizen using nothing more than their mobile phone number.
How Proxyearth Works
Launched in October 2025, Proxyearth asks users to input a mobile phone number, then returns detailed information linked to that number. It pinpoints the target’s location on a map similar to Google Maps. But it doesn’t stop there. The site displays full biodata of the individual, including:
- Full name
- Father’s name
- Email address
- Telecom provider
- House or flat number
- Building or society name
- Alternate mobile numbers
- Postal code, city and district
- Plain text Aadhaar card number
Hackread.com tested a private mobile number belonging to a friend. The site returned accurate and up-to-date details, raising serious concerns about how easily personal data can be exposed without consent. This isn’t just a breach of privacy; it shows how vulnerable millions of Indian citizens may be to tracking and surveillance.
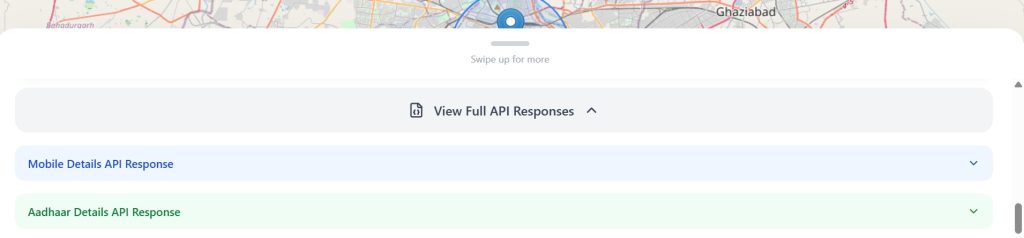
There’s also an option labeled “View Full API Responses”, which reveals even more. One section shows a Mobile Details API Response, and another contains an Aadhaar Details API Response.
Both View Full API Responses expose additional data such as linked email accounts, secondary addresses, extra phone numbers and other personal identifiers. This level of detail suggests the tool is using data from past KYC leaks, possibly leaked Aadhaar databases, and other state-linked data sources.
However, while the exact backend of Proxyearth remains unclear and we are intentionally not sharing the link for privacy and security reasons, there are only a few realistic explanations.
One possibility is insider access from within the Indian telecom sector, where employees may have exposure to subscriber data at scale. A more likely scenario is that the tool is pulling from past breaches involving telecom companies or government-linked databases.
For context, in January 2024, Hackread.com reported how a 1.8TB database was being sold on cybercrime forums. The dump allegedly contained names, phone numbers, addresses, and Aadhaar numbers of 750 million Indian mobile users, nearly half of the country’s population. The origin of this database was never officially confirmed, but the scale and structure match what tools like Proxyearth now appear to use.
In another case, back in February 2021, a hacking group known as Red Rabbit Team claimed to have breached Bharti Airtel, one of India’s largest telecom operators. They alleged access to millions of customer records, including Aadhaar card scans and personal details. Airtel publicly denied any breach, but the attackers released partial samples as proof.
For your information, Aadhaar is India’s national ID system, which assigns a unique 12-digit number to every resident. It is linked to biometric and demographic data.
The “About Us” Section of Proxyearth
A look at Proxyearth’s About Us page reveals an obvious attempt to downplay what the tool actually does. It brands itself as a basic “mobile number tracking” site for Indian users, suggesting it simply helps people find general information tied to a phone number. Nowhere does it mention that the site exposes highly sensitive personal data, including full names, Aadhaar numbers, residential addresses and even building-level geolocation.
There is zero mention of where this data comes from, who operates the platform, or whether any of it is legal. There’s no privacy policy, no disclosure of third-party APIs, and no accountability.
By calling itself a “tracker” and leaving out any reference to the real scope of its capabilities, the site clearly aims to lower suspicion. It leans into the language of convenience while quietly enabling large-scale data exploitation. The omissions are deliberate and speak to the intent to keep the tool running without scrutiny from regulators, platforms, or security researchers.
A Direct Threat to Indian National Security
The existence of a tool like Proxyearth isn’t just a privacy disaster; it poses a direct threat to national security. If accurate geolocation, Aadhaar numbers, and full identities of Indian citizens can be pulled by anyone with a phone number, it opens the door to large-scale surveillance, profiling, and targeting.
Law enforcement officials, government employees, military personnel, whistleblowers, fact-checkers, and journalists are equally exposed. In the wrong hands, this level of access can be easily used for espionage and even destabilization efforts in some cases.
