Red Hat published security advisory CVE-2025-10725, detailing an Important severity flaw in the OpenShift AI Service that could enable low-privileged attackers to elevate their permissions to full cluster administrator and compromise the entire platform.
With a CVSS v3 base score of 9.9, this vulnerability poses a critical risk for organizations leveraging Red Hat OpenShift AI for machine learning workloads.
Privilege Escalation Vulnerability (CVE-2025-10725)
The root cause of CVE-2025-10725 lies in an overly permissive ClusterRoleBinding associating the kueue-batch-user-role with the system:authenticated group.
In typical deployments, data scientists and other authenticated users access Jupyter notebooks and AI pipeline features with minimal privileges.
However, by exploiting this misconfiguration, an attacker can invoke the batch.kueue.openshift.io API to create arbitrary Job and Pod resources.
Inject malicious containers or init-containers that execute oc or kubectl commands, chain privilege elevation within the cluster by binding newly created service accounts to higher-privilege roles.
Ultimately, assume the cluster-admin role and gain unrestricted read/write access to all cluster objects. This exploit completely undermines the confidentiality, integrity, and availability of hosted workloads, allowing theft of sensitive data, service disruption, and full infrastructure takeover.
| Risk Factors | Details |
| Affected Products | Red Hat OpenShift AI 2.19 (RHEL 8)Red Hat OpenShift AI 2.21 (RHEL 9)registry.redhat.io/rhoai/odh-rhel8-operatorregistry.redhat.io/rhoai/odh-rhel9-operator |
| Impact | Privilege escalation |
| Exploit Prerequisites | Valid authenticated user accountAccess to OpenShift AI ServiceLow-privileged account, Access to Jupyter notebook or similar interface, Ability to interact with batch.kueue.openshift.io API |
| CVSS 3.1 Score | 9.9 (Critical) |
Mitigations
Red Hat has released fixes in the following errata, updating the OpenShift AI Operator for Red Hat Enterprise Linux 8 and 9:
- RHBA-2025:16984 (OpenShift AI 2.19 on RHEL 8)
- RHBA-2025:16983 (OpenShift AI 2.21 on RHEL 9)
Administrators should apply these updates immediately. As a workaround before patching, remove the problematic ClusterRoleBinding:
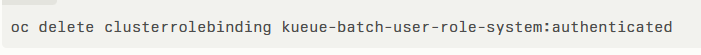
Then, grant job-creation permissions explicitly to trusted identities. This approach enforces the Principle of Least Privilege, ensuring only designated users or groups can submit AI jobs.
Red Hat classifies CVE-2025-10725 as Important rather than Critical because the attacker must hold a valid authenticated account, albeit with low privileges.
Nonetheless, the impact remains severe. Organizations running Red Hat OpenShift AI should remediate promptly to prevent complete cluster compromise and adhere to hardened RBAC configurations going forward.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
