Dutch security researchers have disclosed a fresh batch of critical vulnerabilities in TETRA (Terrestrial Trunked Radio) networks, including flaws that undermine its end-to-end encryption (E2EE) used by intelligence agencies and special forces.
Netherlands-based security consultancy Midnight Blue dubbed the new set of flaws it discovered via reverse-engineering as 2TETRA:2BURST.
The new research exposes six additional security flaws in the widely adopted emergency services radio standard, adding to the five vulnerabilities the same team found in 2023.
Among these, the most serious new vulnerability, CVE-2025-52941, shows that TETRA encryption algorithm ID 135 uses an intentionally weakened AES-128 implementation.
This reduces the effective encryption strength from 128 bits to just 56 bits, making it vulnerable to brute force attacks.
Another critical flaw, CVE-2025-52943, affects networks that support multiple encryption algorithms.
When the weak TEA1 algorithm is supported alongside stronger ones like TEA3, attackers can exploit the easily cracked TEA1 key that offers just 32 bits strength instead of 80 bits, to decrypt traffic from supposedly secure algorithms.
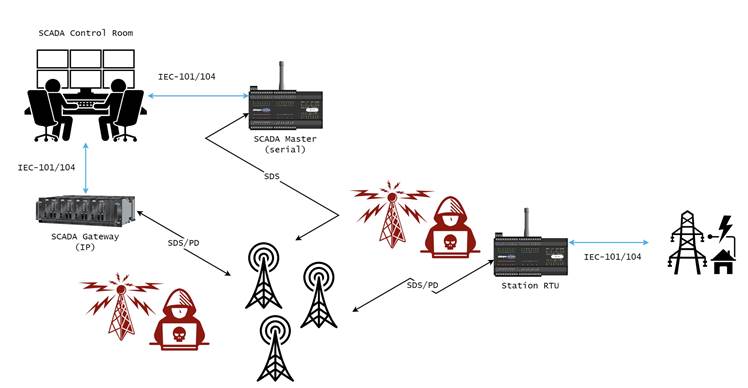
The research demonstrates how attackers could inject malicious data traffic into TETRA networks used for industrial control systems.
In mining environments, this could potentially allow hackers to manipulate SCADA systems that control critical equipment like conveyor belts or processing plants.
Mitigation difficult
Unlike software vulnerabilities that can be patched with updates, many of the newly discovered flaws seem to stem from fundamental design decisions in the TETRA standard itself, such as lack of message authentication and replay protection.
The end-to-end encryption vulnerabilities specifically affect the Sepura Embedded E2EE solution, though researchers believe other TETRA E2EE implementations may face similar issues.
TETRA cryptographic algorithms remained secret for nearly three decades, preventing the independent security research that typically identifies such flaws in open standards,
Plans for the publication of the algorithms were announced in 2023, ending a “security by obscurity” strategy by the European Telecommunications Standards Institute (ETSI) which standardised TETRA in 1995, following Midnight Blue’s earlier research.
“The widespread adoption of TETRA, the often sensitive nature of communications, and TETRA’s dubious track record (including the backdoor in TEA1), highlight the necessity of a thorough independent assessment,” the Midnight Blue researchers wrote.
“This became even more pressing since E2EE is considered a mitigation for our previous TETRA:BURST vulnerabilities,” they added.
TETRA networks operate in more than 100 countries and serve as the backbone for police, fire, and ambulance communications across Europe and many other regions.
Australian mining companies have moved to TETRA for communications across vast remote operations over the past decade.
Midnight Blue’s research team presented their findings at the recent Black Hat USA 2025 security conference in Las Vegas.