The RTM Locker ransomware gang has been discovered to utilize a Linux encryptor that focuses explicitly on virtual machines on VMware ESXi servers, making it the most recent instance of an enterprise-oriented ransomware attack.
Uptycs’ Threat Intelligence unit uncovered the RTM Locker threat faction while conducting dark web reconnaissance.
Since 2015, the RTM cybercrime group has been involved in financial fraud, using a custom-made banking trojan to steal money from their targets.
Trellix cybersecurity firm and Uptycs recently revealed that RTM Locker initiated a new Ransomware-as-a-Service (RaaS) venture, actively hiring affiliates, including ex-Conti cybercriminals.

Technical Analysis
RTM Locker and Babuk ransomware share commonalities, such as ECDH Curve25519 for asymmetric encryption and random number generation.
However, Babuk uses sosemanuk, while RTM Locker uses ChaCha20 for asymmetric encryption, which differentiates the two.
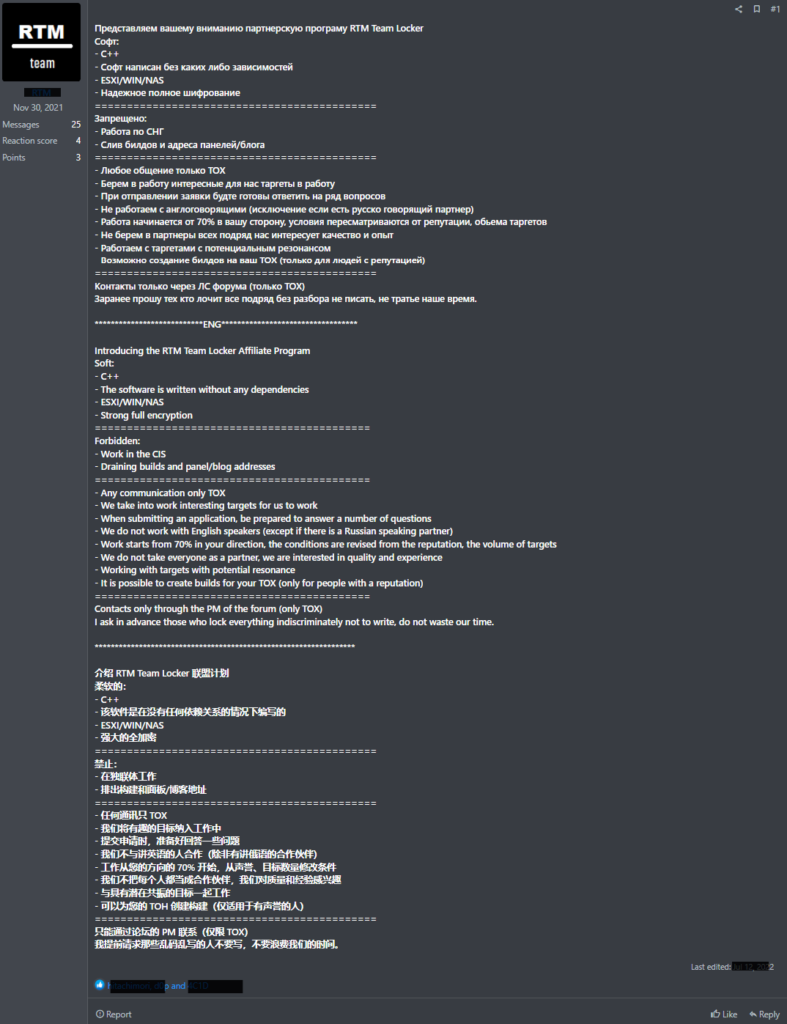
Upon initial inspection of the ransomware binary, it became apparent that the program was tailored towards ESXi due to two ESXi commands at the beginning of the code.
The binary is statically compiled and stripped, which allows it to run on various systems and makes reverse engineering a challenging task.
Moreover, the initial access vector remains unknown, adding a layer of complexity to the situation.
While in this binary, the most important functions are:-
- name_threads
- run_esxi_commands
- pthread_wrapper_main
Here below, we have mentioned the two ESXi commands that are run using this program:-
- esxcli vm process list >> vmlist.tmp.txt: This command lists all the ESXi VMs currently running on the system.
- esxcli vm process kill -t=force -w: This command kills all the ESXi VMs that were found by the previous command.
Due to enhance oversight capabilities and superior resource management, businesses have migrated to virtual machines (VMs) in recent years.
This results in organizations typically utilizing dedicated devices and VMware ESXi servers hosting multiple virtual servers to manage their infrastructure.
Following this trend, ransomware operations have developed Linux encryptors tailored to targeting ESXi servers, which can comprehensively encrypt all enterprise data.
Furthermore, the RTM Locker Linux encryptor seems to be designed explicitly for assaulting VMware ESXi systems, given the numerous references to commands employed in VM administration.
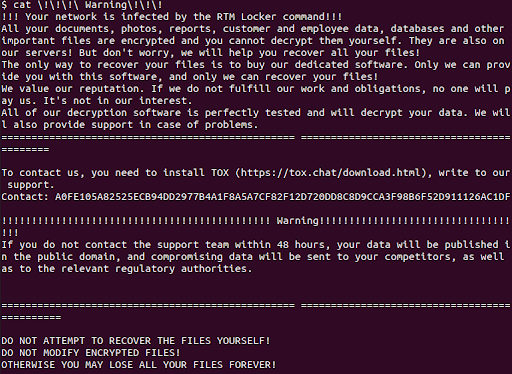
Ransom Note
As part of its file encryption routine, the encryptor modifies the names of the affected files by appending the “.RTM” extension.
Following the completion of the encryption process, the malware proceeds to generate ransom notes on the compromised system, which are typically labeled as:-
After encrypting the victim’s files and appending the “.RTM” extension to their names, the ransom notes issued by the attackers typically contain threats to publish the stolen data if the victim fails to pay a ransom.
These notes also instruct the victim to contact RTM’s “support” within 48 hours via the anonymous messaging platform Tox to initiate negotiations for the ransom payment.

Historically, RTM Locker relied on TOR payment negotiation sites to communicate with victims and demand ransom payments.
However, the attackers have recently shifted their communication strategy and begun using the anonymous messaging platform TOX.
The development and deployment of an ESXi-targeting variant of the RTM Locker ransomware indicate that this threat actor poses a significant risk to enterprise-level organizations.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus





